Digital Transformation: What It Is and How It Helps Your Business
Technology continues to evolve and more companies than ever before are pursuing digital transformation. They’re using new tools and processes to take full advantage of the modern technologies and systems available to organizations of all sizes.
But what exactly is digital transformation, and how can it help your business thrive in today’s market? LI Tech Solutions answers both of these questions and more in detail.
Digital Transformations | LI Tech Solutions Breaks it Down
Digital transformation means something different to every organization. But overall, it involves transitioning your company’s current tech stack to a modern tech stack, as well as leaning further into modern digital technology use.
For example, a company might practice digital transformation by taking advantage of cloud technology and data storage. Using these tools, the company then enables most of its employee base to work remotely.

It can include adjustments or alterations to processes and procedures, using new tools instead of old ones, and changing company culture to adapt to modern digital technology.
The Four Areas of Digital Transformation
Broadly speaking, there are four primary areas of digital transformation. Your organization may see changes in all of these areas or just some of them.
Collaboration Transformation
Digital collaboration transformation occurs as you use collaboration and project management platforms ranging from Microsoft Teams to Microsoft 365 and more. Even communication platforms like Slack can help you enact a shift toward digital collaboration transformation.
Think of this element of transformation as shifting the way your team members collaborate and do work together, even when not in the same office environment.
Business Transformation Consultant’s Guide: Microsoft vs Google Workspace in Long Island, NY
Disaster Recovery & Business Continuity Transformation
Digital transformation also affects disaster recovery and business continuity. Cloud security, new antivirus software, and adaptable IT infrastructure are all some of the rewards that come from pursuing digital transformation.
Digital transformation processes enable organizations to be flexible, adaptable, and more secure. Furthermore, organizations can be more responsive and ensure that employees maintain productivity even in the event of a data crash, website failure, or security breach.

Cybersecurity Transformation
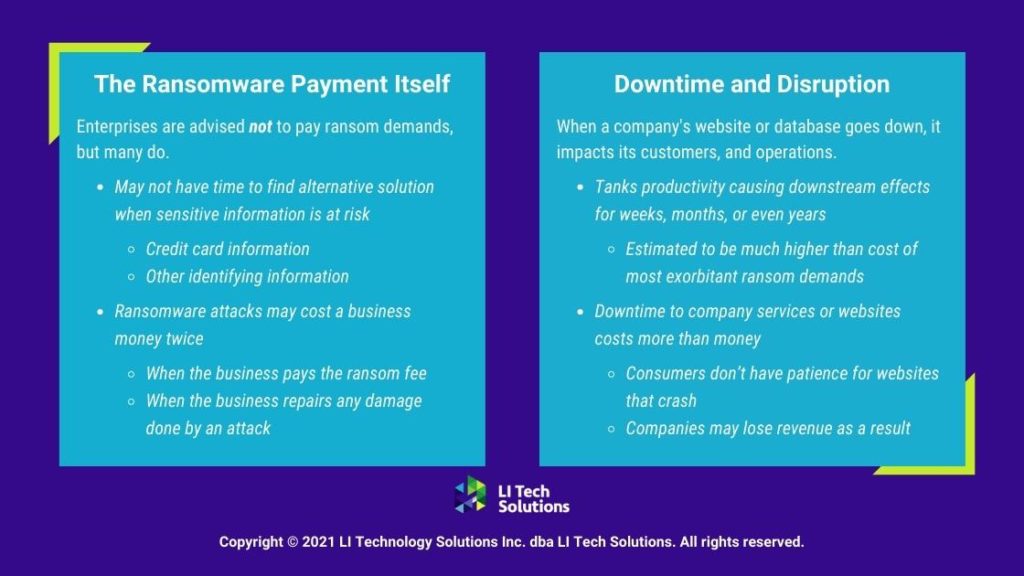
Speaking of security, digital transformations impact cybersecurity massively. As your business goes increasingly digital, cybersecurity solutions such as digital hygiene processes, cloud security, and managed security services all become more important.
This is just one of the many reasons why managed IT services providers such as LI Tech Solutions are valuable to modern organizations. Managed service providers can take care of your cybersecurity needs without massively ballooning your company budget or resource requirements.
Cloud Transformation
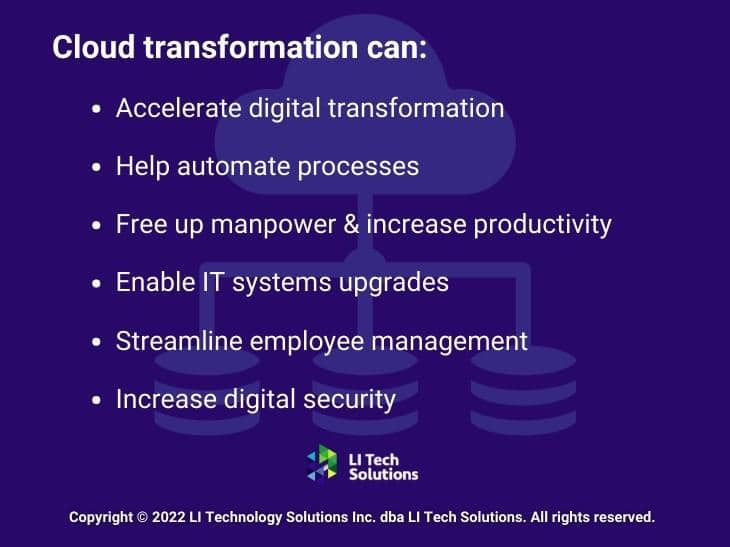
Lastly, digital transformation heavily impacts company cloud usage. Cloud computing can accelerate digital transformation and help your business automate more processes than ever, freeing up additional manpower and leading to greater productivity.
Furthermore, cloud technologies enable you to upgrade your IT systems, streamline employee management and hiring practices, and enjoy greater digital security.
Each of these areas is important and should be pursued by your company at the earliest opportunity.
Trends and Predictions in IT Outsource Services for Microsoft AI
How Does Digital Transformation Help Your Business? New York’s Best MSP Answers
What about specific benefits that digital transformation brings to your company? There are six major advantages that you might see after transforming your company digitally in the above four areas.
Improved Resource Management
Firstly, your company could see improved resource management. As you leverage cloud technologies and other digital transformation tools, your data and important company files will be more secure and organized.
Your company will be better able to integrate applications and databases into centralized repositories. These repositories, in turn, will enable faster data access and management even from employees around the world.
Better Data Collection and Analytics
Furthermore, transforming digitally will allow your company to collect more data and analyze it with more accuracy. You can create systems to gather the right data, not just any data, and incorporate it into your business intelligence efforts at high levels.
Using automation tools, new data storage techniques, and other practices, you’ll understand your target audience better, track important KPIs more efficiently, and see other benefits.
Better Customer Experience
Even better, digital transformation allows your company to provide a better customer experience across the board. Tools such as chatbots, for example, enable faster customer service response times for your website visitors.
New digital tools also enable you to customize the customer experiences you provide to site visitors. Better customer experiences mean more profits for you in the long run.
Digitization of Culture
Your company’s culture will change for the better. For example, remote work tools and a digital-first workplace both allow your company employees to work anywhere around the world without compromising security or productivity.
In turn, this may enable you to broaden your candidate search for top team members and make your company a more attractive place to work.
More Productivity and Profits
Digital transformation should lead your company to more productivity and profits, as well. As employees do great work from around the world and take advantage of streamlining tools, they’ll get more work done in the same amount of time plus spend less time on rote, monotonous tasks best left to automation technology.
More productivity, of course, oftentimes leads to more profits both in the short and long term.
Increased Agility
Lastly, your company will benefit from boosted agility as it digitally transforms. You can improve your speed-to-market for new products, plus adopt continuous improvement or CI strategies.
The result? More innovation and adaptation to adjust to evolving market and customer demands.

Contact LI Tech For The Best MSP in Long Island, NY
All in all, digital transformation is a net benefit for all organizations, including your own. You can accelerate this transformation for your company by taking advantage of managed services providers like LI Tech Solutions.
As a trusted IT managed service provider in Long Island, New York, we’re well-equipped and ready to assist with your digital transformation efforts from start to finish. Whether you need managed security, cloud server administration, upgrades, or something else entirely, we can help.
Contact us today for more information and further details on how we can help your business transform.