Data Protection in the Cloud: Challenges and Best Practices 2024
As businesses on Long Island, NY, continue to harness the power of the cloud, understanding the intricacies of cloud data security becomes increasingly important. Despite these concerns, only 20% of organizations assess their cloud security in real time. There needs to be a more proactive defense for Long Island businesses. This article discusses the critical challenges and best practices for securing your cloud data to protect against cyber threats.
The Biggest Challenges For Your Cloud Data Security in 2024
Working through the issues associated with cloud data security in 2024 comes with unique challenges. Businesses on Long Island, NY, struggle with the complexities of safeguarding their digital assets in the cloud. We understand these challenges at LI Tech Solutions and are here to guide you through them. Here are the top challenges you face when it comes to cloud data security:
- Data Loss and Leakage: One of the biggest concerns for 69% of organizations is data loss and leakage that can devastate your business. Ensuring your data remains intact and confidential requires constant attention to security protocols and infrastructure resilience.
- Privacy and Confidentiality: You face challenges associated with protecting your business’s sensitive information by avoiding unauthorized access and exposure. That allows you to maintain trust and compliance.
- Accidental Exposure of Credentials: Around 44% of companies risk mishandling credentials. These types of slip-ups can lead to unauthorized access, requiring strict control measures and awareness training.
- Insufficient Real-time Security Posture Assessment: The lack of continuous assessment can lead to overlooked vulnerabilities and delayed responses to threats.
- Qualified Personnel Shortage: The cloud security sector needs help finding skilled professionals. This gap can result in misconfigured cloud-managed services and heightened security risks.
Navigating these challenges demands expertise and experience. LI Tech Solutions offers comprehensive data protection and cybersecurity support. We help you venture into secure and successful cloud computing.

Preparing for Tomorrow With the Best Practices in Cloud Data Security
Once you understand the challenges, you can implement the right cloud data security measures to protect your business. Our focus is empowering your Long Island business with the knowledge and tools to protect your cloud infrastructure against modern threats.
1. Implementing Robust Authentication and Access Controls
Cloud data security requires robust authentication and access controls. Despite the known risks, 43% of organizations do not have mandatory multi-factor authentication (MFA) for console users. This can leave a gaping hole in your security posture. MFA reduces the risk of unauthorized access by combining something you know (like a password) with something you have (like a smartphone app that generates a one-time code).
You should prioritize establishing clear protocols that dictate who can access various data tiers. Tailoring access ensures that sensitive information remains secure and only your employees with a legitimate need have access. That strengthens the overall cloud data security framework.
2. The Role of Encryption in Cloud Security
Encryption is a critical safeguard for cloud data security. Encrypting data with protocols like AES and secure communication protocols like SSL/TLS protects your business against cyber threats. Your data remains undecipherable to unauthorized entities even if intercepted. Considering the intricate nature of digital threats, effectively employing encryption preserves the integrity and confidentiality of your sensitive business data. In tech-savvy areas like Long Island, NY, it is even more important to integrate these encryption standards into your cloud security strategy to protect your digital assets from evolving cybersecurity risks.

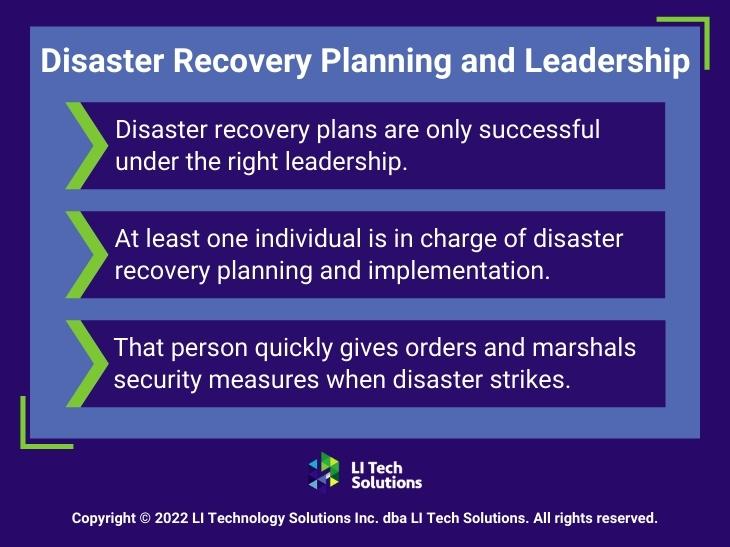
3. Proactive Monitoring and Auditing: The Backbone of Cloud Security
Additionally, the dynamic nature of cloud computing requires continuous monitoring and auditing to detect and respond to security incidents as quickly as possible. Establishing a system that offers real-time visibility can make the difference between a secure cloud environment and a compromised one. This proactive approach allows companies to identify threats and remediate them quickly.
Ultimately, this protects the integrity of your cloud-based assets. Incorporating regular audits and monitoring systems for businesses leveraging cloud data protection solutions ensures that security protocols adapt to new threats. This creates a robust defense mechanism to safeguard against the sophisticated cyber threats that target valuable data in the cloud.
4. Preparing for the Inevitable Through Data Protection Provider Incident Response
When it comes to cloud data security, having a solid incident response plan is non-negotiable. When a security event such as a data breach, DoS attack, or account compromise occurs, the speed and effectiveness of your response mean everything. You must identify your critical assets and establish documented procedures for swift and effective analysis, containment, remediation, and recovery.
Running periodic incident response simulations helps fine-tune your strategy, so your team can act decisively under pressure. These proactive measures for securing data in the cloud help minimize the impact of security incidents while maintaining trust and ensuring business continuity.
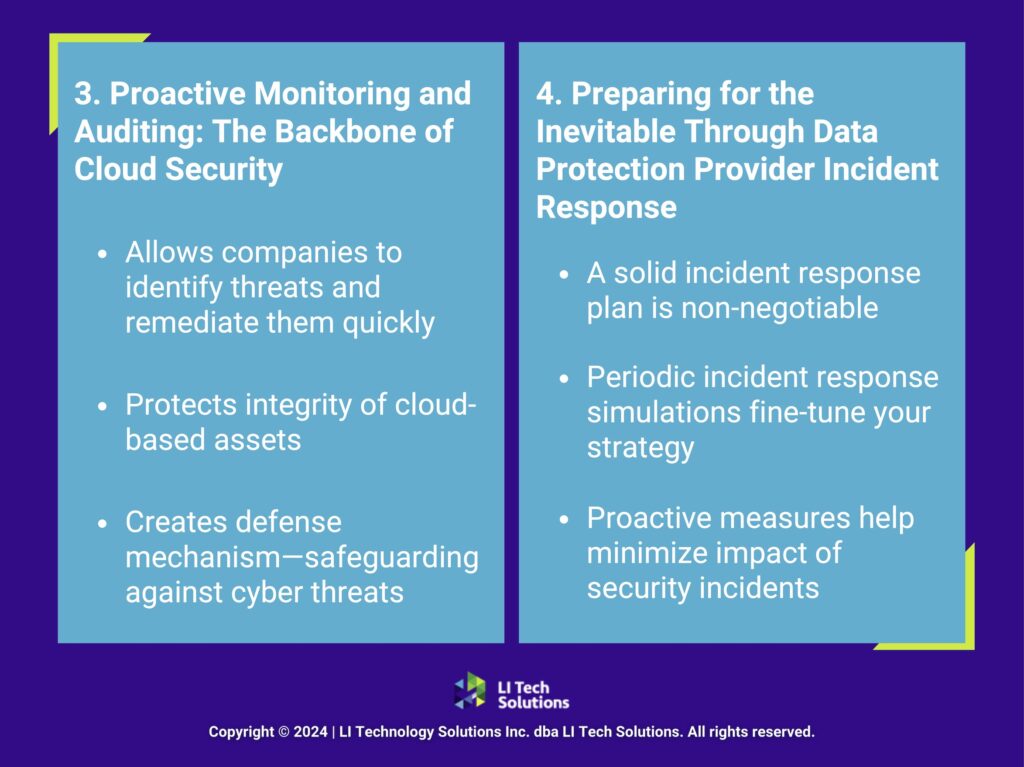
5. Compliance Controls: Navigating Regulatory Requirements
In sectors like healthcare and finance, adhering to compliance standards in cloud data security is necessary and a mandate. Stringent data security, privacy, and sovereignty regulations govern these industries. Familiarizing yourself with relevant compliance frameworks and identifying necessary controls such as storage encryption, access management, network security, and logging is fundamental.
Regular audits to validate these controls are essential in demonstrating your commitment to regulatory compliance. This proactive approach helps avoid costly legal ramifications and reinforces your reputation as a trustworthy and compliant organization.
6. Fostering a Security-Conscious Culture on Long Island, NY
Creating a security-conscious culture within your organization is paramount for effective cloud data security. It’s about more than just protocols—it’s about embedding security-minded practices throughout your organizational fabric. Education on cloud security risks and responsibilities should be an ongoing effort, integrating these principles from the early stages of application development through to daily operations.
Developing comprehensive playbooks that outline tailored cloud-use policies and procedures enhances the security framework. Encouraging best practices in access management, remote work, and password policies fortifies your organization’s defenses. Your cloud infrastructure stands resilient against the evolving threats in the digital world.
7. Partnering With the Right Data Protection Cloud Providers
Choosing a reputable cloud security provider bolsters your organization’s defenses and cloud infrastructure. Top providers like Microsoft and AWS don’t just deliver tools but entire enterprise data loss protection solutions designed to address complex challenges. These providers continually update their services to combat the latest cyber security threats, offering you cutting-edge protection.
Integration with these providers means access to advanced threat detection, incident response capabilities, and compliance management tools. For your business on Long Island, NY, partnering with such providers means securing your operations against a landscape of evolving cyber risks. This strategic alliance not only strengthens your security posture but also empowers you with the resources to focus on core business activities, knowing your data security in cloud infrastructures is in expert hands.
Microsoft Business Applications vs. Google Workspace: How LI Tech Can Help

Strengthening Cloud Security in 2024 With LI Tech’s Advanced Cloud Security Solutions
LI Tech Solutions stands at the forefront of cloud data security and IT support for businesses, offering advanced solutions to safeguard your digital assets. As a leading managed IT services provider on Long Island, we are ready to enhance your digital defenses. Want to find out how your business can benefit from these cloud security best practices? Contact us today for a free consultation and propel your business into a secure digital future.