What Is Compliance as a Service?
Cloud computing and its underlying technologies have changed or challenged every business precept most of us are familiar with. The ”as a Service” moniker has been developed in a variety of industries. Marketers are now using “XaaS” or “Everything as a Service” to confuse everyone.
A concept with global implications and staying power is the emerging industry of Compliance as a Service. No matter the industry or company size, each organization must adhere to some form of law or regulation as part of its operations.
Compliance as a Service is an emerging technology and industry that may soon be needed by a majority of the world’s businesses. The following post highlights recent developments in regulatory compliance and defines what CaaS brings to the table.
- Regulatory Compliance
- Compliance as a Service
- Four Verticals That Are a Fit for CaaS
- Industries Needing a CaaS Provider

Regulatory Compliance
Compliance mandates touch every industry on earth. The five most regulated industries in the United States:
- Petroleum and coal manufacturing
- Electric power generation, transmission, and distribution
- Motor vehicle manufacturing
- Nondepository credit intermediation
- Depository credit intermediation
In our daily lives, regulatory compliance touches each one of us in some way or another. A majority of people have no clue about the guidelines we follow.
For example, manufacturing concerns must comply with the Occupational Safety and Health Administration (OSHA). If you went grocery shopping today, the food you purchased is regulated by the Food and Drug Administration, Health and Human Services, or Department of Agriculture.
Simply put, a business must follow regulations set by the state, federal, and international law. Specific requirements depend largely on the industry and type of business. Regulatory compliance helps drive accountability in the workplace.
Businesses are finding efforts to stay compliant extremely difficult; because an industry environment shifts, and businesses must tweak their approach, Again. Compliance targets constantly evolve.
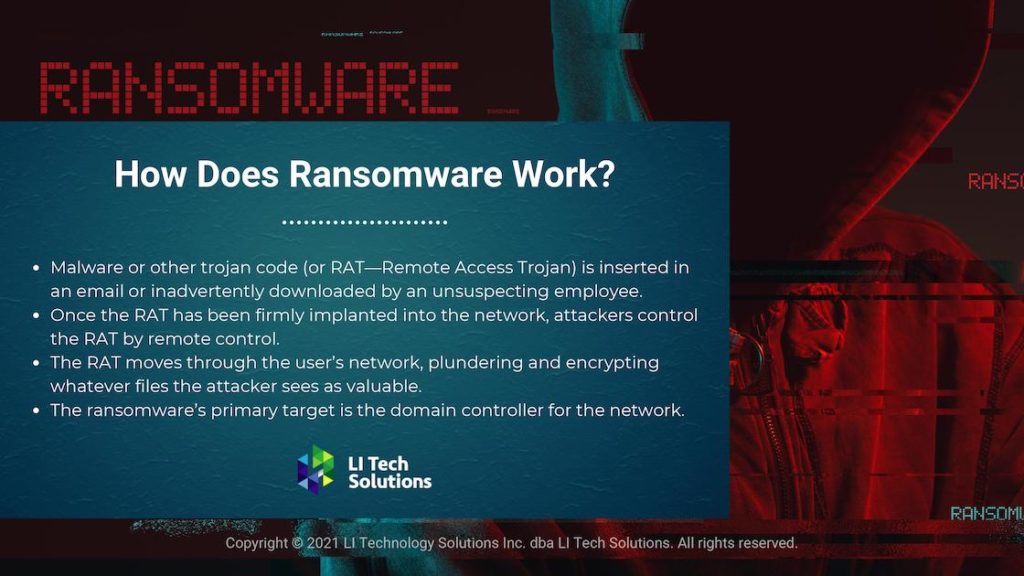
Hackers probe vulnerable networks in every corner of the globe. Ransomware is taking a massive toll on infrastructure as the government seems ill-prepared for the onslaught.
Years of cybersecurity apathy have led to staggering increases in pirate attacks. Heavily regulated industries are turning to organizations offering regulatory compliance.

Compliance as a Service | Get The Best CaaS with Long Island Tech Solutions
Compliance as a service is a relatively new entrant in the market with international implications. CaaS offerings are designed for companies in intemperate industries such as banking, healthcare, and automotive.
CaaS is a cloud-based contract specifying how an MSP will help an organization meet its regulatory mandates. The goal of a CaaS provider is to reduce a company’s regulatory burden.
CaaS providers may feature several solutions. These methods may include assessing a company’s current regulatory governance, develop risk and compliance strategies, and help the organization create strategies that support compliant best practices.
Transparency is the name of the game for CaaS providers. Companies offering regulatory assistance are developing complex services to meet the growing demand.
Cybersecurity complacency has many companies and governments playing catch-up to some of the best coders in the world. December 2020, United States authorities are still trying to unravel a broad cyber-attack on nine government agencies and over 100 companies. The MEP National Network is the government’s answer to rampant cyber threats in manufacturing.

Industries Needing a CaaS Provider
Keeping data safe is creating a compliance nightmare for multinational conglomerates. Before long, every business on earth may need some form of compliance service or, at the very least, a compliance officer.
Businesses face a growing landscape of changing regulations with the ever-evolving threat of cyber-attack. Non-compliance is not an option and can result in sizable fines, loss of customers, and in extreme cases, business closure.
Long Island Tech Solutions Identifies Four Industries Perfect For CaaS services:
- Healthcare must successfully deal with HIPAA, or they have no chance of staying in business. HIPAA compliance deals with a number of regulatory mandates, such as periodic auditing of every file on the books. Developing formal policies, employee training, documentation, and associate management can bury a medical office if not prepared. Plus, there are strict requirements in case of data breaches.
- Government contractors are required to protect unclassified information. (CUI) The business must protect sensitive information, control permissions, and respond to security threats, among other regulations.
- Retail is another industry that may need regulatory services sooner than later. If the business accepts credit cards, they must protect the card holder’s personal information. Regulations require a firewall, antivirus, and encryption. Compliant policies must be in place in case of an audit.
Manufacturing covers a broad range of disparate scenarios. Requirements are equally broad in their regulations which include environment, health, safety, and industrial hygiene. Quality management such as the ISO9001 standard may also need to be met.