What IT Services for Small Businesses Should Offer in NY
Reliable IT services are no longer a luxury for small businesses on Long Island. Whether managing customer data, supporting remote staff, or preventing downtime, having the right IT partner can make or break your business operations.
Small business owners often face challenges like cybersecurity risks, outdated software, and limited internal resources. Without the right IT support, these issues can quickly grow into serious problems.
This guide covers the most important questions to ask when evaluating IT service providers. These insights are designed to help Long Island small businesses avoid costly mistakes, find a provider that aligns with their operations, and ensure their technology actually supports growth. Choosing IT services for small businesses on Long Island shouldn’t feel overwhelming. If you’re exploring your options, consider scheduling a free 15-minute consultation with LI Tech Solutions to receive expert guidance and practical answers, with no pressure and no bots. We’ll help you determine if we’re the right fit, or connect you with someone who is.
Why Small Businesses on Long Island Need Professional IT Support
Small businesses face growing pressure to secure their data, stay compliant with regulations, and manage more complex systems with limited staff. Adding remote work and region-specific risks, such as storm-related outages, makes it clear that professional IT support isn’t optional.
Outsourced IT services for small business clients can fill these gaps. Managed IT services for small businesses offer predictable support, proactive security, and technology planning. Instead of reacting to problems, your business can focus on growth. For a broader context, the U.S. Census Bureau provides official small business statistics that highlight the importance of reliable operations and planning for SMBs nationwide.
Key Questions to Ask Before Hiring IT Services for Small Businesses on Long Island

1. Do You Have Experience Working with Small Businesses Like Mine?
Not all providers understand the needs of small businesses. Ask whether they’ve worked with businesses of your size or in your industry. The IT needs of a medical office or nonprofit are very different from those of a large corporation.
One-size-fits-all solutions often miss the mark. Look for a provider who builds systems around your actual workflows.
2. What Is Your Onboarding Process Like?
Some providers set you up quickly, but without a thorough understanding of your systems. That leads to gaps, confusion, and unexpected costs.
At LI Tech, onboarding starts with an audit. We visit your site, assess your environment, and develop a customized plan tailored to your specific needs.
3. Do You Offer Local Support on Long Island?
Many managed services providers in NYC or upstate New York operate remotely. That might work for some, but Long Island businesses often need in-person support.
Ask if a technician can come on-site when needed. Local providers like LI Tech can respond faster and build a more personal partnership.
4. What Is Included in Your Managed Services Plan?
Clarify what the provider includes: monitoring, patching, endpoint protection, backups, and helpdesk support. You should know exactly what you’re getting.
Some providers offer only fixed packages. Others allow customization based on your environment.
If you’re searching for IT support for businesses that fits your budget and setup, get that list upfront.
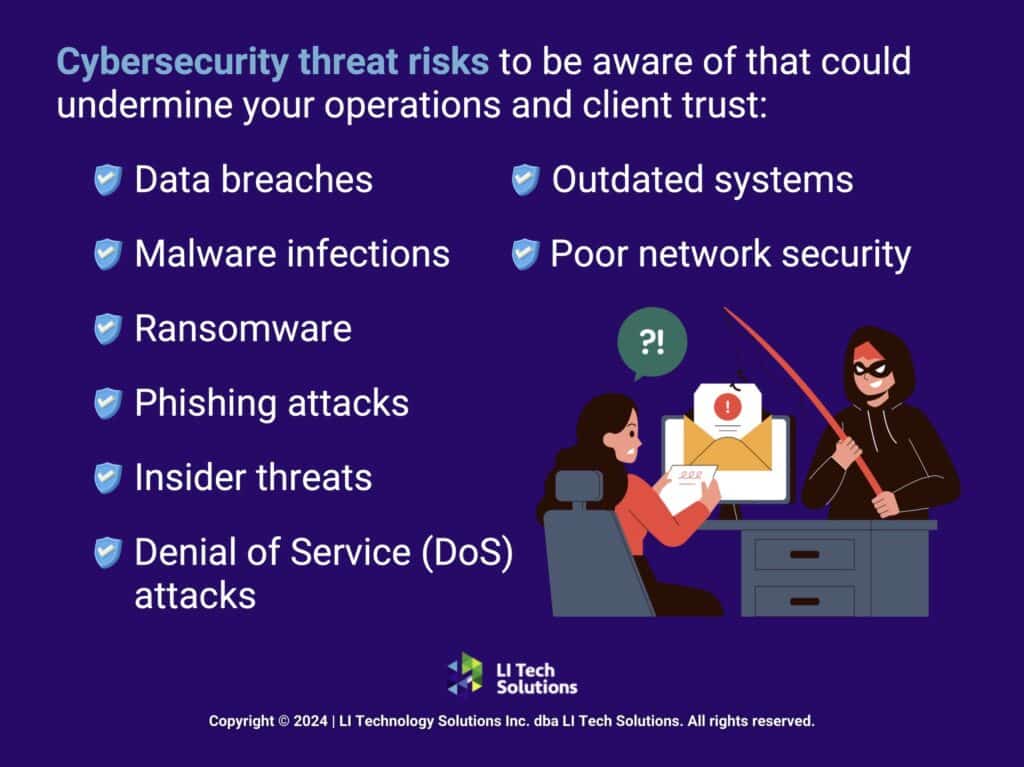
5. How Do You Handle Cybersecurity and Data Protection?
Security is non-negotiable. Ask how they protect against threats like ransomware and phishing. Do they offer employee training? What about compliance with regulations like HIPAA or the SHIELD Act?
Cybersecurity firms that support small businesses should offer layered protection, including monitoring and recovery plans, in addition to antivirus software.
6. Can You Support Remote Work and Mobile Devices?
If your team works from home or uses mobile devices, ask about Mobile Device Management (MDM).
At LI Tech, we support Addigy, Cisco MDM, and Apple Business Manager. That means we can secure your mobile fleet, protect remote workers, and even assist with Apple hardware procurement.
7. How Transparent Are Your Pricing and Contracts?
Avoid providers who hide pricing behind long sales cycles or “starting at” ranges. You should know what to expect before signing anything.
At LI Tech, we provide upfront, ballpark pricing during your initial call. If it’s not the right fit, we’ll point you in the right direction, no hard sell.

Warning Signs to Watch for When Choosing IT Services for Small Businesses
- Vague service details or unclear contract terms
- No mention of in-person support or Long Island presence
- Heavy use of buzzwords without specifics
- Promises of “guaranteed uptime” with no written SLA
These are signs the provider may not be a good long-term fit. Learn more about how to choose an IT Company on Long Island from this guide.
Comparing Local IT Options in New York
Not all providers serve Long Island the same way. Here’s what to consider:
- Long Island: Look for responsive, local teams who can visit your site when needed
- NYC: Many providers are high-volume and remote-focused
- Upstate New York: Often remote-only, with fewer small business specialists
Are you looking for a custom software development company in New York? Comparing managed services providers in NYC? Not sure if IT managed service providers in upstate New York offer local support? These are the kinds of differences that matter.
LI Tech Solutions, based on Long Island, is designed to meet the IT needs of small businesses. We’re a local, responsive, and easy-to-reach team.

What to Expect When Working with LI Tech Solutions
- Real technicians, not bots or outsourced call centers
- A discovery-first process with on-site audit and a scoped proposal
- Experience supporting healthcare, nonprofit, and compliance-heavy industries
- Deep Apple expertise: Addigy, Apple MDM, Cisco tools
- Clear proposals and frictionless quoting
We don’t just manage your IT. We help you make better technology decisions.
Conclusion: IT Services for Small Businesses on Long Island
Choosing the right IT partner starts with knowing what to ask. Look for experience, transparency, and local support, not just a sales pitch. A trustworthy IT provider should make it easy to understand what’s included, how they’ll support your growth, and how they respond when something goes wrong. Don’t settle for vague promises or overly technical jargon. Focus on who will be managing your systems, how accessible they are, and whether they’re committed to small business success.
Ready to talk to someone who understands the IT needs of Long Island small businesses? Book a free 15-minute consultation with LI Tech today and get honest answers, no bots, no pressure.