Global Impact of Cybercrime: What Every Business Needs to Know
Cybersecurity companies are having a banner year on Wall Street, and why not? Deadly threats to business are popping up almost daily, threatening people’s lives and income. The global impact of cybercrime requires a business to understand the emerging trends of cybersecurity.
Cybercrimes’ threat to business costs the global economy over $445 billion each year, while intellectual property theft exceeds $160 billion. Threats against small businesses are alarming. One in five fall victim to cybercrime, and of those, 60% are out of business in 6 months.
Cybercriminals went on a crime spree during the pandemic and have taken advantage of the world’s dependence on technology.
Li Tech Solutions (516) 210-6400
Will the Constant Threat of Cyberattack Ever End?
What began as a small network for scientists and researchers a few short decades ago has turned into an $8 trillion behemoth connecting over 3.5 billion people. The internet has become an essential aspect of people’s lives around the globe.
Businesses of every size rely more on the internet than ever before. Data and connectivity are the lifeblood of small businesses. The internet allows the smallest firms in remote locations to have a global impact.
As networks expand and new technologies come online, cybercrime is expected to grow. According to Cisco Umbrella’s 2021 Cybersecurity Trends, the statistics are alarming. These numbers are from Cisco devices and services that process over 620 billion internet requests daily.
- 86% of organizations had at least one user try to connect to a phishing site.
- 70% of users were served malicious browser ads.
- 69% experienced some form of unsolicited crypto mining offer.
- 50% of every organization encountered some ransomware activity.
- 48% found information-stealing malware activity on their network.
Li Tech Solutions (516) 210-6400

A majority of experts queried on “Why are businesses so vulnerable to cyberattack?” The single gravest answer – Human Error!
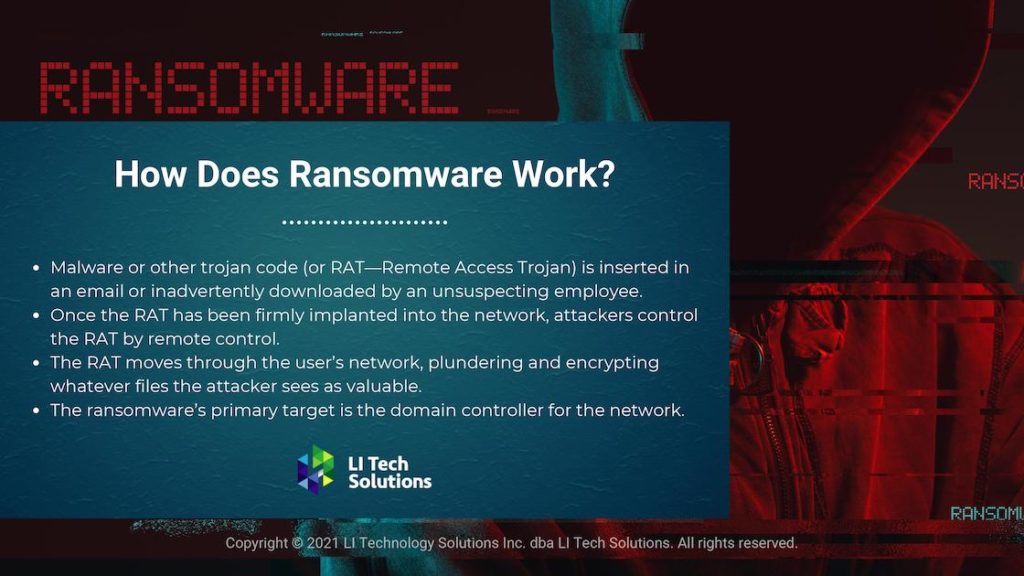
Businesses are vulnerable and have the most to lose. In the latest round of ransomware attacks, the cybercriminals target large infrastructure companies with a lot to lose if their operations were interrupted. They are holding companies hostage.
According to the FBI’s Internet Crime Report for 2020, email scams reported to the bureau accounted for most of the damage to businesses. The FBI’s report described several devastating scams, such as the BEC/AEC email hoax, which dealt with the fraudulent transfer of funds.
Cybercriminals gained access to business accounts through social engineering techniques and direct computer intrusion.
Cyberattack
Small businesses with limited resources are lucrative targets for cybercriminals seeking credit card numbers, bank accounts, and employee financial data. Smaller companies tend to have weaker security measures because more transactions are online via the cloud. Small businesses generally ignore the dangers and impact of cybercrime in favor of daily profit.
Cyberattack Methods:
- Hacking: email and system hacking are the two of the most common methods for cybercriminals to gain access and manipulate company information.
- Phishing: Unsuspecting employees pass along personal and sensitive information to fraudulent websites.
- Social Engineering: employee trust is built with fraudulent interaction to gather more information.
- Malware: malicious software is increasingly more effective and dangerous as employees do not recognize the threat.
- Keylogging: software tracks employee keystrokes and is dangerous because some anti-virus programs cannot detect the threat.
- Identity Theft: stealing an employee’s personal information and using it to commit fraud is becoming easier for cybercriminals.
So much has been written about cybersecurity, it is becoming difficult for individuals and businesses to know how to proceed. The single best step a business can take, partner with Li Tech Solutions and let them guide you in the right direction.
Li Tech features five modules that can help a small business have a global impact.
Protect Your Business
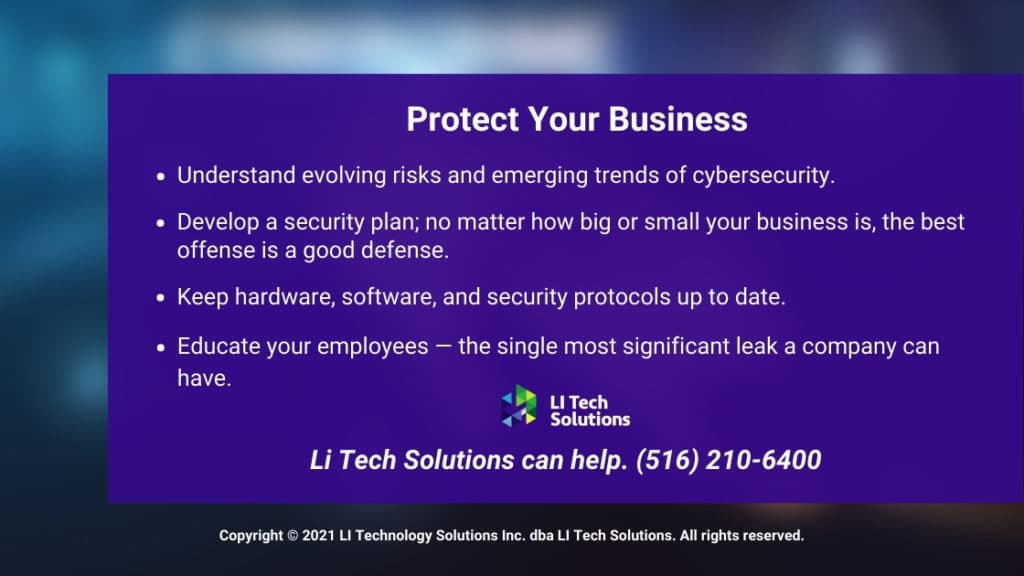
Understand evolving risks and emerging trends of cyber-security and be prepared for the vulnerabilities in your business. Know what is valuable to a cyber-criminal; credit cards, asset accounts, intellectual property.
Develop a security plan; no matter how big or small your business is, the best offense is a good defense. Make sure every digital protocol is covered when making your plan. Cover the routine actions employees perform daily, like data backups. Include newer technologies that impact your operation, such as social media and cloud computing.
Keep hardware, software, and security protocols up to date. Li Tech Solutions can be a big help.
Educate your employees on the impact of cybercrime. Every piece of advice written about cybersecurity includes some form of educating an employee. Mainly because employees are the single most significant leak a company can have, IT staff and management should not be the only ones concerned about cybersecurity.