Stop! And think, before you act on that email
Don’t fall victim to cyber criminals. We explain what a BEC attack is and how to protect your business.
Don’t fall victim to cyber criminals. We explain what a BEC attack is and how to protect your business.
There’s a setting in Edge that sends the images you view online to Microsoft. We give you all the details.
Free VPNs may seem tempting, but they could be exposing your data to cyber criminals. We tell you how to protect your business.
What Is Data Protection? Why It’s Important and Why Cybersecurity Can’t Be Separate
Ransomware is one of the most pervasive and dangerous forms of malware or computer virus. Not only is it dangerous for individual desktops and mobile devices, but it can be positively catastrophic for businesses of all sizes in Long Island, NYC.
A ransomware attack occurs when a virus installs itself on a device, like a desktop or phone. It finds and encrypts sensitive data or locks down the device completely unless a ransom is paid, usually in cryptocurrency like Bitcoin.
Unfortunately, many business owners believe that they are safe from ransomware, or believe other harmful myths about this digital threat. Today, we’ll bust four myths about ransomware so you’re better equipped to protect yourself and your business in the future.

Many small to mid-sized business owners erroneously believe that their enterprises are safe from ransomware attacks. They think ransomware cybercriminals only target big businesses with tons of customers and lots of extra money in the bank. This is not true in the slightest.
In truth, most ransomware attackers don’t know the identities of their victims. They send out ransomware attacks, such as phishing emails, rather indiscriminately. If they get anyone to install the virus on a computer terminal, they’ve succeeded. Most individuals don’t know what to do, and will pay the ransom out of desperation.
According to a Cybersecurity Special Report by the U.S. Chamber of Commerce and RSM, 23% of middle-market company executives reported at least ransomware ransom or attack in 2022. This demonstrates how any brand can be vulnerable to ransomware attacks, not just big businesses.
If you think your small business is safe just because you’ve been fortunate enough not to run into a ransomware attack yet, think again. Sooner or later, you and your employees will know what to do when you’re targeted (albeit blindly) by a ransomware-armed cybercriminal.
By nature, each ransomware virus demands a ransom from its victim. Some business owners and individuals think that paying the ransom demand is safer, especially if the ransom message says that the criminal will delete sensitive data or expose sensitive files if payments aren’t made ASAP.
In truth, you should never pay a ransom demand if a device is infected with a ransomware virus. Ransomware creators can’t be trusted – they’re criminals, after all. More importantly, there’s nothing stopping those criminals from carrying out whatever ill ideas they have in mind after you fork over the cash.
It’s a much better idea to work with incident response or IR cybersecurity specialists. They can deal with ransomware attacks, evaluate the situation, and help you get access to sensitive data quickly without having to pay the bad actors. Even if paying the ransom is the right move, you should only do it with a cybersecurity negotiator on your team.
Whatever you do, don’t keep a ransomware attack to yourself. Inform your employees or your cybersecurity specialists so the proper response can begin at the earliest opportunity.

Strong antivirus software is certainly a great tool in your overall digital defense toolkit. However, it won’t universally keep yourself or your company safe from ransomware and other malware attacks.
The truth is that digital defenses must constantly keep up with newly evolving viruses and cyber attack threat vectors. Even the best antivirus firewall can have gaps in its armor from time to time. Therefore, a new ransomware virus that hasn’t been detected and studied before might slip through and attack your business’s sensitive files.
Furthermore, many ransomware attacks occur through antivirus software because of employee negligence. One of the most common vectors for ransomware is a phishing email, which is a scam email that installs a virus onto a user terminal when it is opened.
Therefore, you can’t just rely on antivirus to keep your enterprise safe. You must also:
It might be tempting to think that backing up your sensitive data is enough to protect you if the worst comes to pass if your business crashes with a ransomware attack. However, backups can’t always be relied upon to save the day, nor can they always protect your brand from reputational damage amongst your customers.
In fact, many cybercriminals now have advanced malicious tactics to compromise backup files, locking them down or deleting them if ransomware victims don’t pay the fines.
So-called double extortion attacks involve cybercriminals encrypting and stealing data at the same time. So even if you do have a backup of key data ready to go, the criminals can still leak that sensitive data unless you pay the demanded ransom.
Given these threats, you shouldn’t merely rely on backups to protect your business and its reputation. Instead, keep the above tips in mind – such as training your employees and hiring cybersecurity specialists – to shore up your business’s digital defenses as much as possible.
Are You Properly Backing Up Your Business Data?

As you can see, ransomware is far more dangerous than you may have initially realized. Even though some of your ideas about ransomware have been busted, remember that you can protect your business and your personal files by working with the right security partners.
At LI Tech, our capable specialists can draw up a list of security best practices for you and your employees to follow. We also offer a spread of managed cloud security services in Long Island, NYC. Contact us today to see how we can keep you safe from ransomware.
Have you ever received a notification on your phone while you’re sleeping, asking if it’s really you logging in?
It’s called a fatigue attack and Microsoft Authenticator’s latest feature will help to protect you.
Bot malware is a worrying new security risk. Malware bots steal whole user profiles – that’s a complete snapshot of your ID and settings.
A typical data breach in the United States costs around $9.44 million—more than twice the global average. Healthcare is the top sector affected by pricey data breaches, but any business can be severely affected. Data protection and cybersecurity should be a top concern for Long Island, NYC business owners. A data breach can threaten your profits, your reputation, your employees, and your customers. It can also put your enterprise at legal risk.
If you’re wondering exactly what data protection entails – and why you should make it a priority – this article will answer some of your questions. It can be hard to distinguish between data protection and cybersecurity measures, since the two are so intertwined. Some people view cybersecurity as a technical field, and data security as more direct safeguarding measures. But this view is an oversimplification of both. We’ll explore the relationship between data protection and cybersecurity, and we’ll also take a look at how LI Tech Solutions can help you shield your business from harm.
Streamlining Healthcare Data Management with Managed IT Services in Long Island

Data protection is the act of shielding your information from unwanted access. You need to take steps to make sure sensitive information isn’t altered or destroyed—or leaked to unauthorized parties. LI Tech Solutions is the best cybersecurity company in Long Island, NYC. So naturally, we handle all aspects of data loss protection, including:
Cybersecurity is a more generalized term that describes the “art” of protecting digital networks, devices, and data and ensuring their privacy and accessibility. Malware, hacking, and the exploitation of programming errors that cause vulnerabilities are just a few of the threats that cybersecurity experts have to combat.
At LI Tech Solutions, we understand that if disaster or sabotage strikes your business, your quick response is critical. Your data doesn’t just sit motionless. It travels from one point to another, and it’s exposed to multiple vulnerabilities along the way. There’s no such thing as data that’s free from any possible threat.
These are some primary reasons you should invest in state-of-the-art data protection for your enterprise.
You probably have access to sensitive data about your team members and customers. Personally identifiable information is a broad category that includes direct identifiers and quasi-identifiers. In other words, it refers to data that can be used on its own to identify a person, or data that can be combined with other bits of information to build an identity.
Direct identifiers include information such as:
Four types of indirect identifiers include:
When you allow unauthorized users to access any personal information, you expose employees and/or customers to identity theft, fraud, and other serious threats.
Understanding IAM in the Modern Cybersecurity Landscape: Challenges and Solutions

The GDPR and CCPA are designed to protect individuals and consumers from harm by regulating entities that access and store their data. The GDPR, or General Data Protection Regulation, applies to all businesses that conduct any transactions within the EU. The CCPA, or California Consumer Privacy Act, safeguards consumers’ rights to control their own personal information. Failure to comply with regulatory bodies that govern your business can lead to legal action and fees: up to $7500 per violation of the CCPA, and a wide range of penalties for violating the GDPR. Clearly, prevention is the best approach.
A data breach can harm your brand’s value and reputation in ways that are hard to repair. Today’s consumers care more about whether their personal information is protected than ever before. If your clients are involved in a data breach, they’ll probably stop giving you their business. Investors are also likely to shy away from companies with a reputation for poor security measures.
Businesses in the United States lose between $180 billion and $540 billion every year when their trade secrets are stolen. On top of that, they’re often subject to hefty legal fees as they seek to rebuild after the damage caused by a data breach. When you lose control of the things that make your business unique, it can be hard to measure the financial losses involved.
Business owners often make the mistake of handling data protection and cybersecurity as two separate entities. However, this approach is costly since it involves multiple teams, and it’s also not the most effective way to ward off threats. Let’s examine a few key reasons.
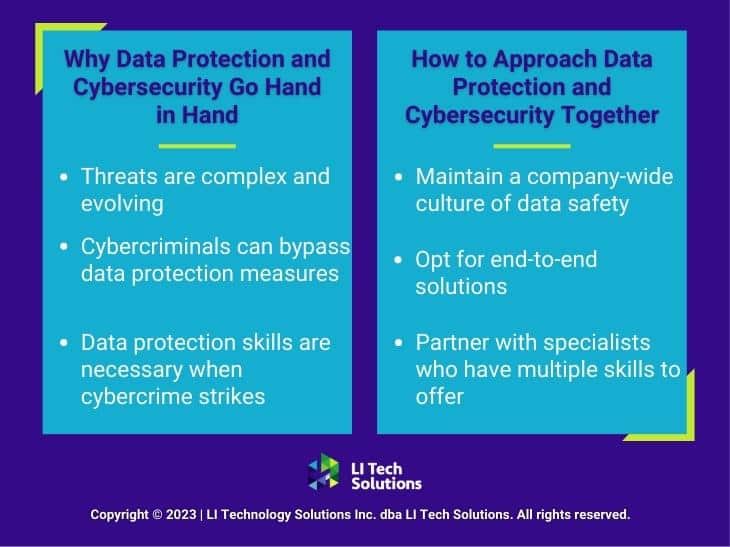
As technology evolves, digital threats become more sophisticated to keep pace. Those with malicious intent will stop at nothing to gain access to your data, and their skill sets are more comprehensive than ever. To stop them, you need a multi-layered approach that integrates data protection and cybersecurity skills.
Data protection solutions are effective for what they’re designed to do. But cybercriminals can sometimes find a way around them. For example, MFA (multi-factor authentication) might protect your devices from access by non-employees. But cybercriminals can conduct a brute force attack to simply figure out both points of authentication through trial and error.
After a major cybersecurity breach, your top priority is making your data secure again. This does mean implementing measures that directly address the source of the breach. But it also means taking a comprehensive approach and revisiting all your data protection policies to safeguard against the next attack.
Cybersecurity Consulting: Navigate Digital Threats With Expert MSP Solutions
We’ve got a few tips that can help you form an integrated approach to protect your business.
When data is handled carelessly, hackers can more easily gain access to your systems. The best way to safeguard your information is to have your data protection and cybersecurity specialists work together – and to frequently educate your entire team about proper procedures.
Ultimately, humans are often the vulnerable points in an organization that bad actors will exploit to access sensitive data. Everyone in your organization – not just your security specialists – is responsible to keep your information safe.
An end-to-end solution is one that provides a complete answer to a problem, without having to rely on external sources. LI Tech Solutions offers end-to-end services that protect your data from start to finish, anticipating and addressing threats on all fronts.
Why hire a team of data loss protection specialists if they can’t handle other cybersecurity needs? Why invest in a cybersecurity partnership if you’ll need to find someone else to handle your data protection? If Long Island government systems are vulnerable to crippling cyberattacks, it’s clear that cybercrime is a significant threat to local businesses, too. Ultimately, the best cybersecurity company in Long Island, NYC will bring a comprehensive skill set to the table.
IT Services for Law Firms In Long Island Boost Productivity and Security
As the best MSP on Long Island, LI Tech Solutions offers all the services you need, without the burden of maintaining full-time IT staff. Is it time to outsource your IT support needs to the experts? Call 516.210.6400 today and ask for a free consultation and technology assessment!
Airports, hotels, cafés, even shopping malls, offer public charging points where you can boost your phone or laptop battery on the go. They’ve been in the news after the FBI recently tweeted advice to stop using them. Crooks have figured out how to hijack USB ports to install malware and monitoring software onto devices as they charge. The security risk …
Read More
One of the many cool things about the new wave of Artificial Intelligence tools is their ability to sound convincingly human. AI chatbots can be prompted to generate text that you’d never know was written by a robot. And they can keep producing it – quickly, and with minimal human intervention. So it’s no surprise that cyber criminals have been …
Read More
Your data is one of your most valuable business assets. Keeping it safe should be one of your main priorities.