Google Calendar Has a Great Update for Hybrid Workers
Want your team to know where you are when you’re not in the office? We explain how Google Calendar’s new feature lets you share multiple work locations each day.
Want your team to know where you are when you’re not in the office? We explain how Google Calendar’s new feature lets you share multiple work locations each day.
LinkedIn is introducing new verification features over the coming months to help tackle fake accounts.
Have you ever received a notification on your phone while you’re sleeping, asking if it’s really you logging in?
It’s called a fatigue attack and Microsoft Authenticator’s latest feature will help to protect you.
Microsoft has just announced an option for people to trial new features before their general release in Windows 11. This isn’t about fixes to security flaws – everyone gets those at the same time. This is an opportunity for businesses to jump the queue to receive new features and updates first. Sound exciting? Yes! Worth the risk? Not quite. Our …
Read More
Every modern organization collects a wealth of data on its customers, clients, and more. But that data must be protected and easily retrieved in the event of an IT infrastructure outage or cyberattack. This guide explains why you should properly back up your business data and how data protection solutions safeguard your data for maximum protection.
Businesses just like yours must back up crucial data for two key reasons:
Imagine a scenario in which you have all your customer relationship data included on a single server. However, that server crashes and the data is lost. At that point, you now have to start from scratch rebuilding your consumer relationships, including the contact information, their preferred methods of contact, and more.

Backing up all business data is important, but two specific types of data are more vital than others.
As touched on above, you must keep sensitive client or customer data secured and backed up at all times. Customer data includes personal identifying information, order histories, personal preferences, and much more.
You’ll also want to protect company-specific data, like passwords for your servers, sensitive organizational information like your order flow or vendor ID codes, and so on.
The last thing you want is a cybercriminal gaining access to sensitive corporate data, then blackmailing you by threatening to release that information to your competitors or your customers.
Read more in our blog: What Is Data Protection? Why It’s Important and Why Cybersecurity Can’t Be Separate

Given the importance of backing up crucial company data, it’s wise to implement a back up policy ASAP. But many companies may not properly back up their business data.
For example, they may simply copy over important files once a month onto a separate hard drive. Or they might use secondary or subpar technologies to back up server files, only to find that a server outage results in most of the data being lost during a single unlucky incident.
If your company hopes to back up data properly, you need to use the right technologies, methodologies, and services. Data protection solutions include:
Read more in our blog: 4 Dangerous Ransomware Myths Proven False
Above all else, the best way to properly back up your business data is to rely on managed services providers like LI Tech Solutions.
As dedicated managed IT services providers in Long Island, New York, our enterprise data protection solutions and other services are just what you need to make sure your data is backed up safely and correctly every single time.
LI Tech’s disaster recovery services are designed to insulate your business and sensitive data from all manner of hazards, ranging from cloud or other technology breakdowns to operator errors to cyber sabotage to environmental calamities and more.
Specifically, we take several key steps to safeguard your data, apps, and systems before that crucial digital information is lost. These steps include:
If your business ever encounters a disaster that causes its infrastructure to collapse or its data to be lost, you can rest assured that LI Tech’s backups will have you “back up” and running in no time.
More than that, LI Tech takes responsibility for scheduling and implementing regular data backups for your organization. With regular backups, all crucial data should be secured on the cloud or elsewhere. You’ll never run into the disaster scenario where sensitive data created or collected a day previously is lost because of an ill-timed server outage.
As an added benefit, when you hire us to schedule your data backup services, your people can focus on other elements of your business.
Data Protection in the Cloud: Challenges and Best Practices 2024

In addition to the above services, LI Tech Solutions will plan and carry out a full IT infrastructure review for your organization if you choose. The infrastructure review can identify:
Armed with this information, we’ll then upgrade or streamline your IT infrastructure depending on what you need. Such improvements can lower the likelihood of data loss entirely or protect your business from catastrophe.
All in all, LI Tech is the number one managed IT services provider on Long Island, NYC. We serve brands just like yours by offering not only disaster recovery and data backup services but also IT security services and more. Contact us today to see how we can help your brand thrive in the modern digital environment!
Bot malware is a worrying new security risk. Malware bots steal whole user profiles – that’s a complete snapshot of your ID and settings.
A system is basically some sort of information technology like apparatus or freeware. Executives of projects and programs often take part in SDLC, alongside system and system programmers, what is system development life cycle architect coders, and even prospective users. The Software Development Life Cycle (SDLC) meaning is a method for creating high-quality, low-cost software in a short amount of time.
Theoretically, this model helps teams to address small issues as they arise rather than missing them until later, more complex stages of a project. The information system will be integrated into its environment and eventually installed. After passing this stage, the software is theoretically ready for market and may be provided to any end-users.
This includes conducting interviews, studying existing processes, and identifying stakeholders’ needs. The gathered information serves as a basis for designing a system that meets users’ expectations and addresses organizational challenges. The report provides valuable information on the production costs, supply chain dynamics, and raw materials that are essential to the Life Cycle Assessment Software market. It also analyses the impact of COVID-19 on the industry and provides recommendations on how businesses can adapt to the changing market conditions.
Systems analysis and design (SAD) can be considered a meta-development activity, which serves to set the stage and bound the problem. SAD interacts with distributed enterprise architecture, enterprise I.T. Architecture, and business architecture, and relies heavily on concepts such as partitioning, interfaces, personae and roles, and deployment/operational modeling to arrive at a high-level system description. This high-level description is then broken down into the components and modules which can be analyzed, designed, and constructed separately and integrated to accomplish the business goal. SDLC and SAD are cornerstones of full life cycle product and system planning. This includes all the specifications for software, hardware, and network requirements for the system they plan to build.
They did not have a proper concept of what the possibilities would be on the short term. This Software Development Life Cycle approach is common for smaller projects with one or two developers. The V-shaped paradigm, also known as the Verification and Validation model, is an offshoot of Waterfall that stresses testing at each stage of development.

Some members do not like to spend time writing, leading to the additional time needed to complete a project. When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
During this stage of the system lifecycle, subsystems that perform the desired system functions are designed and specified in compliance with the system specification. Object-oriented analysis and design (OOAD) is the process of analyzing a problem domain to develop a conceptual model that can then be used to guide development. During the analysis phase, a programmer develops written requirements and a formal vision document via interviews with stakeholders.
However, it is vulnerable to early delays and can lead to big problems arising for development teams later down the road. Depending on the skill of the developers, the complexity of the software, and the requirements for the end-user, testing can either be an extremely short phase or take a very long time. Take a look at our top 10 best practices for software testing projects for more information.
The System Development Life Cycle (SDLC) provides a well-structured framework that gives an idea, of how to build a system. It consists of steps as follows- Plan, Analyze, Design, Develop, Implement and Maintain. We will delve into the significance of each stage, emphasizing the critical role played by System Design in the overall process. After training, systems engineers and developers transition the system to its production environment.

Many organizations subdivide their SDLC methodologies into a larger number of phases than the five referenced in NIST guidance, potentially offering closer alignment of SDLC phases and corresponding RMF tasks. As such, the move is done during off-peak hours, to ensure a minimal impact on business operations. Both professionals and end-users should be able to reap the benefits of the new system during this phase. During the fifth phase the system is installed in the production environment.
As it is still challenging to go back and make changes, this model is best used when there are no unexpected requirements. In contrast to other structured SDLC approaches, Waterfall’s approach to completing each stage before moving on to the next is the simplest and most time-tested. Although the switch is complex and fraught with uncertainty, the danger is reduced significantly because it is typically implemented during off-peak hours. This is the point at which both end-users and system analysts should be able to see the fruits of your labors in the form of a polished, fully functional project. Web application and API protection (WAAP) in any customer environment — all via one integrated platform.

Process checks include review of timelines and expenses, as well as user acceptance. The 2023 “Life Cycle Assessment Software Market” research report meticulously explores industry segmentation by Types [Cloud Based, On-premises], Applications [Large Enterprises, SMEs], and regional dynamics. This comprehensive analysis illuminates the current market landscape, spotlighting emerging trends, and untapped opportunities under the market dynamics section. Moreover, it unveils the market’s CAGR status, with its historical and future performance. Once when the client starts using the developed systems, then the real issues come up and requirements to be solved from time to time.
Developers have to follow the coding guidelines described by their management and programming tools like compilers, interpreters, debuggers, etc. are used to develop and implement the code. The next phase is about to bring down all the knowledge of requirements, analysis, and design of the software project. This phase is the product of the last two, like inputs from the customer and requirement gathering.
If productivity tools aren’t embedded properly within your business, tasks can actually end up taking longer than they should.
Microsoft is planning to enable Multi-Factor Authentication (MFA) directly in its Outlook app for many 365 business users.
A typical data breach in the United States costs around $9.44 million—more than twice the global average. Healthcare is the top sector affected by pricey data breaches, but any business can be severely affected. Data protection and cybersecurity should be a top concern for Long Island, NYC business owners. A data breach can threaten your profits, your reputation, your employees, and your customers. It can also put your enterprise at legal risk.
If you’re wondering exactly what data protection entails – and why you should make it a priority – this article will answer some of your questions. It can be hard to distinguish between data protection and cybersecurity measures, since the two are so intertwined. Some people view cybersecurity as a technical field, and data security as more direct safeguarding measures. But this view is an oversimplification of both. We’ll explore the relationship between data protection and cybersecurity, and we’ll also take a look at how LI Tech Solutions can help you shield your business from harm.
Streamlining Healthcare Data Management with Managed IT Services in Long Island

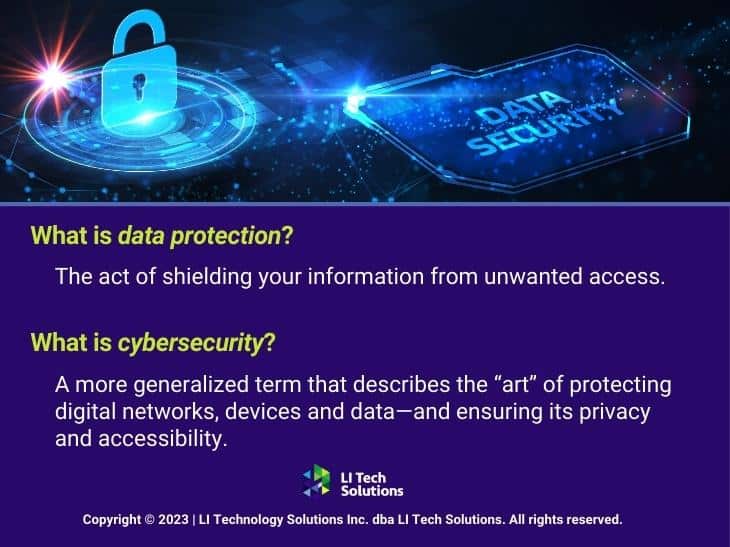
Data protection is the act of shielding your information from unwanted access. You need to take steps to make sure sensitive information isn’t altered or destroyed—or leaked to unauthorized parties. LI Tech Solutions is the best cybersecurity company in Long Island, NYC. So naturally, we handle all aspects of data loss protection, including:
Cybersecurity is a more generalized term that describes the “art” of protecting digital networks, devices, and data and ensuring their privacy and accessibility. Malware, hacking, and the exploitation of programming errors that cause vulnerabilities are just a few of the threats that cybersecurity experts have to combat.
At LI Tech Solutions, we understand that if disaster or sabotage strikes your business, your quick response is critical. Your data doesn’t just sit motionless. It travels from one point to another, and it’s exposed to multiple vulnerabilities along the way. There’s no such thing as data that’s free from any possible threat.
These are some primary reasons you should invest in state-of-the-art data protection for your enterprise.
You probably have access to sensitive data about your team members and customers. Personally identifiable information is a broad category that includes direct identifiers and quasi-identifiers. In other words, it refers to data that can be used on its own to identify a person, or data that can be combined with other bits of information to build an identity.
Direct identifiers include information such as:
Four types of indirect identifiers include:
When you allow unauthorized users to access any personal information, you expose employees and/or customers to identity theft, fraud, and other serious threats.
Understanding IAM in the Modern Cybersecurity Landscape: Challenges and Solutions

The GDPR and CCPA are designed to protect individuals and consumers from harm by regulating entities that access and store their data. The GDPR, or General Data Protection Regulation, applies to all businesses that conduct any transactions within the EU. The CCPA, or California Consumer Privacy Act, safeguards consumers’ rights to control their own personal information. Failure to comply with regulatory bodies that govern your business can lead to legal action and fees: up to $7500 per violation of the CCPA, and a wide range of penalties for violating the GDPR. Clearly, prevention is the best approach.
A data breach can harm your brand’s value and reputation in ways that are hard to repair. Today’s consumers care more about whether their personal information is protected than ever before. If your clients are involved in a data breach, they’ll probably stop giving you their business. Investors are also likely to shy away from companies with a reputation for poor security measures.
Businesses in the United States lose between $180 billion and $540 billion every year when their trade secrets are stolen. On top of that, they’re often subject to hefty legal fees as they seek to rebuild after the damage caused by a data breach. When you lose control of the things that make your business unique, it can be hard to measure the financial losses involved.
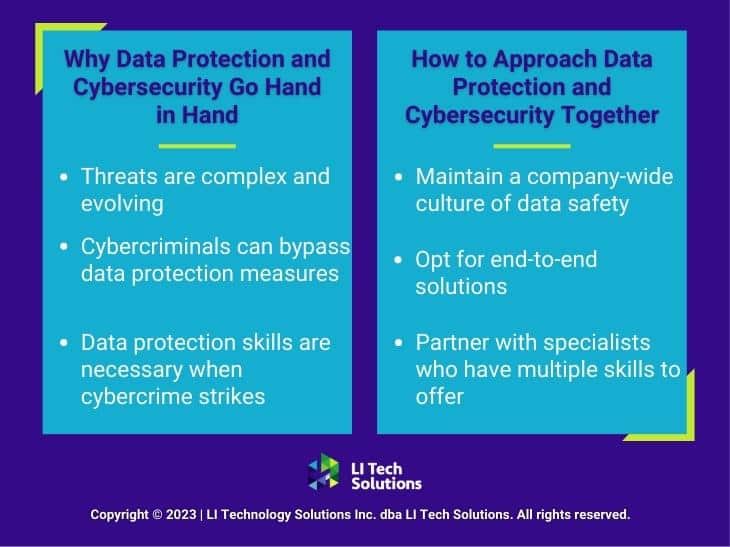
Business owners often make the mistake of handling data protection and cybersecurity as two separate entities. However, this approach is costly since it involves multiple teams, and it’s also not the most effective way to ward off threats. Let’s examine a few key reasons.
As technology evolves, digital threats become more sophisticated to keep pace. Those with malicious intent will stop at nothing to gain access to your data, and their skill sets are more comprehensive than ever. To stop them, you need a multi-layered approach that integrates data protection and cybersecurity skills.
Data protection solutions are effective for what they’re designed to do. But cybercriminals can sometimes find a way around them. For example, MFA (multi-factor authentication) might protect your devices from access by non-employees. But cybercriminals can conduct a brute force attack to simply figure out both points of authentication through trial and error.
After a major cybersecurity breach, your top priority is making your data secure again. This does mean implementing measures that directly address the source of the breach. But it also means taking a comprehensive approach and revisiting all your data protection policies to safeguard against the next attack.
Cybersecurity Consulting: Navigate Digital Threats With Expert MSP Solutions
We’ve got a few tips that can help you form an integrated approach to protect your business.
When data is handled carelessly, hackers can more easily gain access to your systems. The best way to safeguard your information is to have your data protection and cybersecurity specialists work together – and to frequently educate your entire team about proper procedures.
Ultimately, humans are often the vulnerable points in an organization that bad actors will exploit to access sensitive data. Everyone in your organization – not just your security specialists – is responsible to keep your information safe.
An end-to-end solution is one that provides a complete answer to a problem, without having to rely on external sources. LI Tech Solutions offers end-to-end services that protect your data from start to finish, anticipating and addressing threats on all fronts.
Why hire a team of data loss protection specialists if they can’t handle other cybersecurity needs? Why invest in a cybersecurity partnership if you’ll need to find someone else to handle your data protection? If Long Island government systems are vulnerable to crippling cyberattacks, it’s clear that cybercrime is a significant threat to local businesses, too. Ultimately, the best cybersecurity company in Long Island, NYC will bring a comprehensive skill set to the table.
IT Services for Law Firms In Long Island Boost Productivity and Security
As the best MSP on Long Island, LI Tech Solutions offers all the services you need, without the burden of maintaining full-time IT staff. Is it time to outsource your IT support needs to the experts? Call 516.210.6400 today and ask for a free consultation and technology assessment!