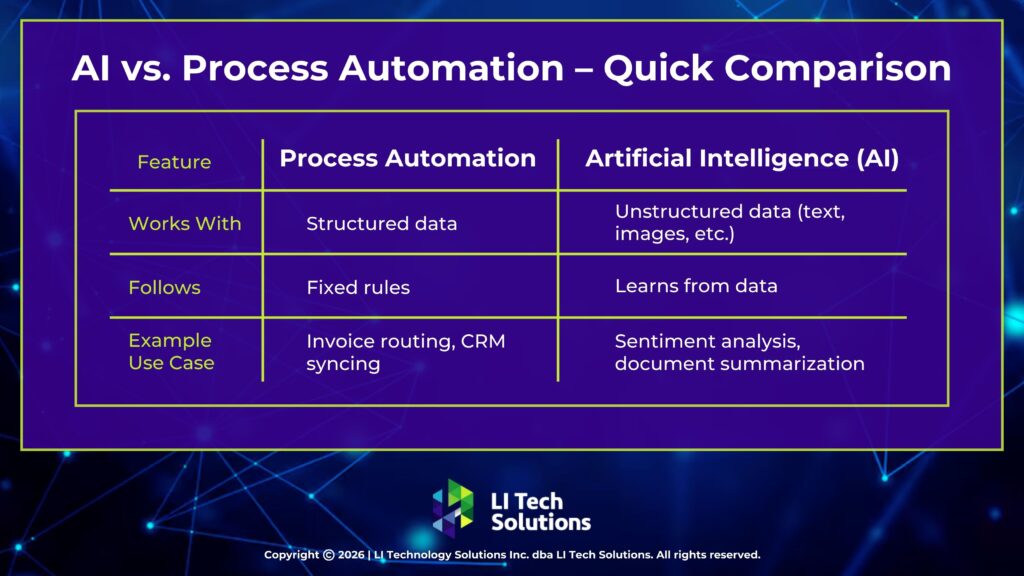
Managed IT Services for Accounting Firms in NY
Accounting firms on Long Island manage high volumes of sensitive financial data and must remain compliant with strict regulations, especially during tax season. When systems go down or security is weak, the risks go beyond lost productivity; they can lead to data breaches, penalties, and loss of client trust.
LI Tech Solutions delivers managed IT services for accounting firms that need reliable, secure, and responsive technology support. We work with firms across Long Island to reduce risk, improve efficiency, and keep operations running without disruption. Schedule your free IT consultation today and discover how we can support your team. Contact us Today or call (516) 210-6400.
Why Accounting Firms Need Managed IT Services
Accounting firms handle large volumes of confidential financial data. A single system failure or breach can result in legal issues, client loss, and reputational damage. Regulatory standards, such as GLBA, IRS Safeguards, and SOC 2, also require firms to adhere to strict data handling and security practices.
Accounting firms often face tech issues that slow down client work, especially during tax season. Managed IT services for accounting firms help by maintaining and updating tools like QuickBooks and NetSuite, reducing disruptions, improving security, and allowing your team to stay productive and focused on clients.
What Managed IT Services Include for Accounting Firms
24/7 System Monitoring and Support
Managed IT services for accounting firms include 24/7 system monitoring to identify and resolve issues before they disrupt your workflow. Whether it’s a network slowdown or a failed update, helpdesk support ensures your team receives quick, expert assistance, so you can stay focused on client work instead of troubleshooting.
Cloud Services for Accountants
Cloud-based software is now standard in many firms. Whether you use QuickBooks Online, Xero, or Intuit Tax Online, managed IT providers help keep those platforms running securely and smoothly. Cloud solutions also enable remote work, protect against local data loss, and facilitate easier client collaboration.
Cybersecurity and Compliance Support
Cyber threats like phishing, ransomware, and email spoofing pose a daily risk to accounting professionals. A managed IT provider strengthens your security by implementing encryption, firewalls, multi-factor authentication, and regular audits. These Cybersecurity consulting services also help ensure that your systems meet the latest IRS and GLBA requirements.

Data Backup and Disaster Recovery
Losing client data during tax season can cost your firm time and trust. Managed IT services for accounting firms include daily backups and fast recovery options to safeguard your files. Both local and cloud solutions ensure that your data meets compliance requirements and remains accessible when it matters most.
IT Consulting for Accounting Firms
Beyond support, accounting firms benefit from IT planning and strategy. Managed IT providers offer consulting to help you prepare for busy seasons, roll out new software, or streamline client portals. This guidance ensures that your technology remains aligned with the firm’s goals.
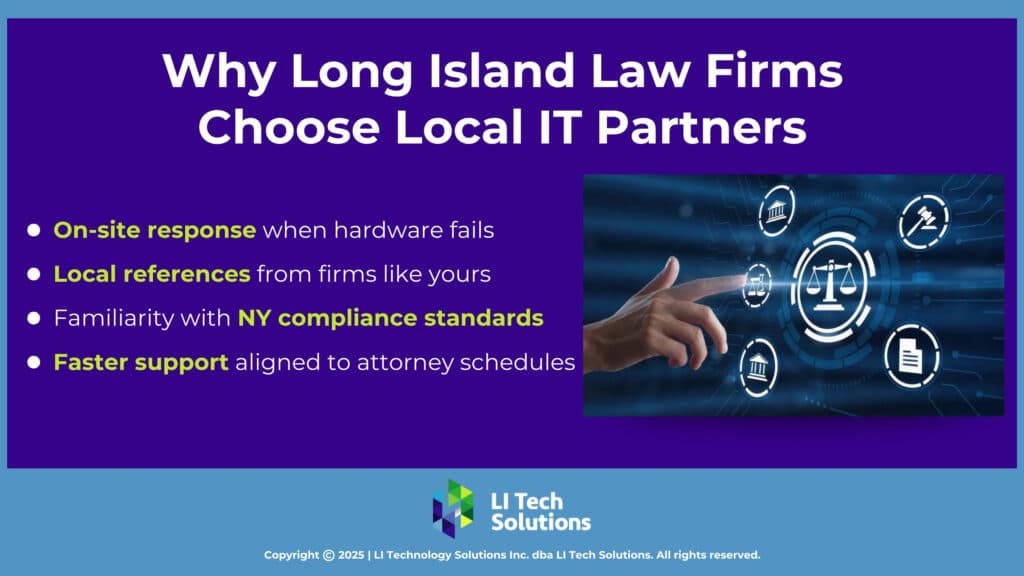
Benefits of Working with a Local IT Partner on Long Island, NY
Partnering with a Long Island-based IT provider delivers distinct advantages. Local teams understand the software and compliance requirements unique to NY accounting firms. They also deliver trusted technology solutions for businesses on Long Island, including onsite support across Nassau, Suffolk, Queens, and Brooklyn when remote help falls short.
LI Tech Solutions, based on Long Island, delivers genuine, local support, never offshore call centers or scripted responses. When your team needs assistance, they connect with professionals who understand the accounting environment.

How to Know If It’s Time to Upgrade Your IT Support
Your accounting firm may benefit from a managed IT upgrade if you:
- Experience regular downtime during tax season
- Don’t have a current disaster recovery or backup plan
- Struggle to manage remote work securely
- Rely on outdated systems or slow support
- Need more reliable IT support for businesses like yours
Why Accounting Firms Choose LI Tech Solutions
LI Tech Solutions provides customized, dependable IT support tailored specifically for accounting professionals. Unlike generic providers, our team works closely with you to understand your needs and develop solutions tailored to your firm’s operations.
- Local, hands-on support throughout Long Island
- Experience with QuickBooks, Lacerte, Xero, NetSuite, and more
- Apple MDM support for firms using Macs or mobile devices
- Co-managed IT options to work alongside your internal staff
- Transparent onboarding and clear expectations from day one

Managed IT Services for Accounting Firms That Fit the Way You Work
LI Tech Solutions offers managed IT services for accounting firms on Long Island. We focus on solving real problems, including cybersecurity risks, outdated systems, and remote access issues. In one call, we’ll review your setup and recommend practical, cost-effective improvements.
Whether you’re facing cybersecurity risks, outdated systems, or remote access issues, we’ll help you identify and address the weak spots and plan ahead. Talk to a real engineer today. Schedule Your Free IT Assessment or call us at (516) 210-6400.