Cybersecurity trends are continually evolving and growing within the powerful frameworks of information technology, the cloud, and network technologies. Over the last few years, rules and procedures have been revised to modernize business operations.
Companies of every size must recognize that cyber threats are a legitimate and ongoing concern that will continue to be part of our everyday lives for years to come.
- SolarWinds
- Cybersecurity in 2021 and Beyond
- Final Word
There are no magic bullets to achievement in business. Owners must now adapt their approach to managing cyber activities to stay ahead of the curve. There has been a flurry of new threats and technologies that have attacked the new stay-at-home mobile workforce.
The remote workforce model has no network boundary, and more applications are written for the cloud than ever. These new network devices, and in most part, poorly written code, give attackers the green light into your business.

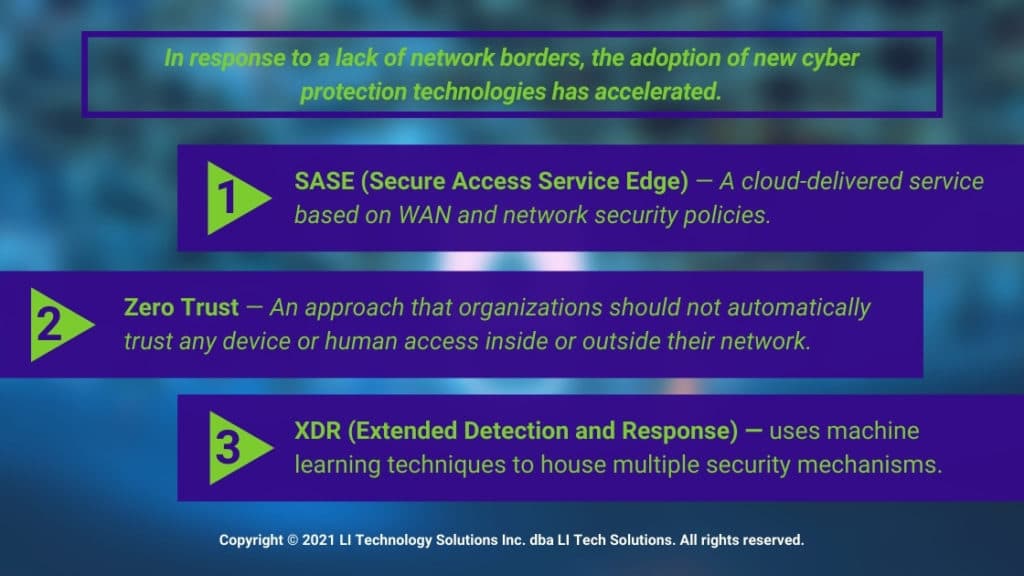
Three Cybersecurity solutions help remote workers control their network.
The world has shifted, and hackers have found lucrative new areas of access to a company’s network. In response to a lack of network borders, the adoption of new cyber protection technologies has accelerated.
- SASE (Secure Access Service Edge) is a real-time context policy for a continuous assessment of risk. SASE is a cloud-delivered service based on WAN and network security policies.
SASE policies can benefit a corporation in several ways, including flexibility with cloud infrastructure, reduced complexity, and cost savings.
- Zero Trust has been part of the technology lexicon since 2010, when the phrase was first introduced. A few years later, Google implemented a Zero Trust Policy for its network. Zero Trust is an approach that organizations should not automatically trust any device or human access inside or outside their network.
- XDR (Extended Detection and Response) is in the early stages of development by several elite vendors. XDR uses machine learning techniques to house multiple security mechanisms. Risk managers are continually overwhelmed with security alerts; XDR helps alleviate these daily pressures.
XDR helps companies improve threat detection and response by centralizing their activity and reducing false positives.
SolarWinds
Washington DC’s worst cybersecurity hack, SolarWinds Orion, has company executives around the world shaking in their loafers. Cyber experts believe there are simply not enough skilled workers to track down all the destruction done to business and government networks.
According to the President of Microsoft, the SolarWinds Orion hack was the most powerful and sophisticated cyberattack ever.
Bruce Schneier, a cyber expert and Harvard fellow, states, “We have a serious problem. We don’t know what networks they are in, how deep they are, what access they have, what tools they left.” The only way to know these infected networks are clean is to burn it down to the ground and rebuild it.”
Three cybersecurity trends have emerged since the SolarWinds attack.
- Microsoft was one of the prime recipients of the mayhem created by SolarWinds. According to authorities, hackers capitalized on the limitations in the authentication architecture of the software giant and its protocols. Microsoft has since rebuilt the vulnerabilities and taken issue with the government’s insistence that more could have been done.
- Cyber Insurance premiums have surged 29% since 2020. Policies for cyberattacks have been in place for a lot longer than most people realize. In 1997, AIG wrote the first cyber insurance policy. Since the SolarWinds incident, cybercrime has increased dramatically, and premiums for cyber insurance have risen approximately 11% annually, with no signs of slowing.
- The cloud, with advanced services and advantages for remote work, has skyrocketed the targets for attackers. Following SolarWinds, attacks on cloud applications have increased and are expected to continue at a torrid pace well past 2021. Misconfigured cloud settings were a significant cause of breaches in 2020, resulting in an average cost of over $4 million to the enterprise.

Cybersecurity in 2021 and Beyond
Every company is now being urged to be proactive in its approach to cybersecurity and the myriad of cyber threats that are coming. Organizations must come to terms with the fact that security is no longer an optional expense but a budget line item.
- Companies must prioritize a cybersecurity workforce. 56% of organizations report a scarcity of personnel for 2021.
- Data continues to multiply every day. Businesses must automate their security processes whenever feasible. In 2020, IBM found a nearly $ 4 million discrepancy in the cost of a data breach between automated companies and those that were not.
Machine learning and AI technologies continue to experience a meteoric rise in complexity and usefulness. These technologies are being developed as part of the enterprise infrastructure to automate security and replace human intervention.
AI influences both sides of cybersecurity trends. Criminals exploit AI and machine learning techniques. Cybercriminals are automating their attacks using data poisoning and model stealing.
Top Cybersecurity Concerns for Long Island Businesses in 2025

Final Word on Cybersecurity Trends
Decades ago and still today, business success requires a lot of open-to-close hours, sweat equity, and plenty of sacrifice. In this digital age, most business owners believe an antivirus program will suffice, and their data records are secure.
Cybersecurity should now be one of the initial steps taken to prepare your organization for success. A healthy distrust of cyber-attackers goes a long way toward keeping company data, intellectual property, and digital assets safe from these criminals.

