If you have been around computers, the word ransomware is a persistent part of your vocabulary. Ransomware is an extortion-based security threat against network infrastructure.
Ransomware is malware code that has been embedded into business and government network infrastructure; controlled remotely by the attacker. The assailant then threatens the victim with either publication or encryption of their data unless they pay a ransom.
It is believed that businesses around the world fall victim to some variant of ransomware every 11 seconds.
Ransomware is part of the protection agenda for every company in the world. From simple code to sophisticated and vicious outcomes, ransomware has become a highly lucrative endeavor for criminal organizations around the world.
- DarkSide
- Ransomware and Its Cost to Business
- Post Breach Mindset
- What’s The Answer
- Recommendations
Call Li Tech Solutions (516) 210-6400 for Answers

DarkSide
Thursday, May 6, 2021, a ransomware attack began on the most extensive pipeline infrastructure in the United States. A cybercriminal group called DarkSide roiled the energy markets and upended the supply of oil and gas to the eastern seaboard of the US. The DarkSide ransomware assault became the most significant cyber-attack on a physical operation in the history of the United States.
Ransomware code was implanted using a focused attack approach. Attacks such as the Colonial Pipeline begin with phishing or spear-phishing designed to steal or activate malware on an undefended machine.
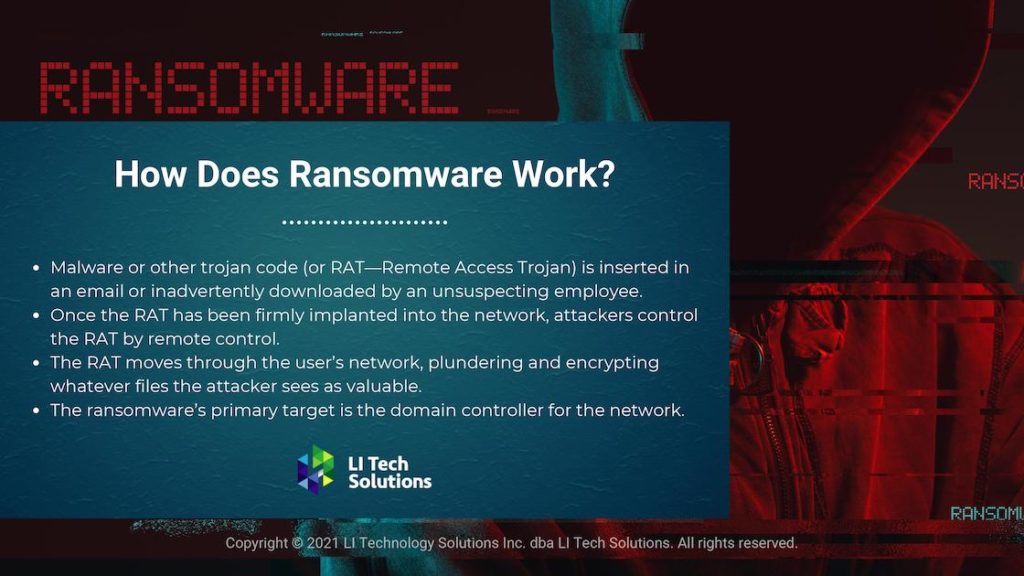
How Does Ransomware Work?
Malware or other trojan code is inserted in an email or inadvertently downloaded by an unsuspecting employee. The implanted malware is called a RAT-remote access trojan. Once the RAT has been firmly implanted into the network, attackers control the RAT by remote control. The command center can be located anywhere in the world.
The RAT moves through the user’s network, plundering and encrypting whatever files the attacker sees as valuable. A decade ago, these techniques were used exclusively by raiders from rogue states and nations. Criminal organizations have become incredibly efficient and profitable with ransomware code. These groups see the assaults on business network infrastructures such as the Colonial Pipeline as highly lucrative.
Attackers behind the DarkSide Ransomware use a power shell to download the binary as an update.exe file. The binary is downloaded into the C:\\Windows directory and creates a shared folder on an undefended machine. The ransomware’s primary target is the domain controller for the network.
Once the domain controller has been conquered, attackers move laterally across the network, securing intelligence and files.
Read more in our blog: 4 Dangerous Ransomware Myths Proven False
Ransomware and Its Cost to Business
The FBI has revealed that in 2020 alone, business losses attributed to ransomware increased an astounding 225%. Organizations that fell victim to attack have a substantial loss of revenue, workforce reduction, and in extreme cases, a complete shutdown of operations.
Even if the organization chooses to pay the ransom, there is no guarantee their data will be returned, and the company is not immune to subsequent assaults.
Li Tech Solutions deploys an expansive array of services to its clients that will answer any perceived or imminent threats. We deal with each challenge head-on, whether the attacker is local or worlds away. Call and speak with one of our security experts. (516) 210-6400
Ransomware Attacks on Business Infrastructure Has Been Significant:
- 2017, FedEx reported losses of roughly $300 million from the NotPetya attack
- The City of Atlanta spent $2.6 million recovering from the SamSam ransomware attack
- Baltimore spent close to $18 million to reconstruct its entire network from another SamSam attack
- Cognizant saw a substantial loss of revenue in 2020 earnings because of the Maze ransomware attack
Every industry vertical is vulnerable to a ransomware attack. The damage to brands and stature is a long-lasting problem for victim companies. Most brands feel they can come back in short order if they have adequate cyber-attack insurance and have complete data backups.
Unfortunately, even if companies purchase cyber-attack insurance, the losses are more catastrophic than what is covered. Ransomware is a pervasive threat and one in which companies of all sizes need to address with urgency.
AI for Business: Top Trends Transforming Operations in 2025

Post Breach Mindset
Many cyber-security experts feel there is no way for businesses to ward off a ransomware attack. It is safer to assume you will be attacked, than wonder if you will.
The fact is, if you wait, you are too late.
In the past several years, there has been a lot of talk about ransomware with little action to back up the talk. Again, experts believe there needs to be an emphasis on new security methods; companies have not developed yet. Unless there is clear direction from government and tech leaders, critical infrastructures remain at risk.
Li Tech Solutions (516) 210-6400
A post-breach mindset means companies need to reset themselves and be prepared for the worst. Companies and governments need an exhaustive research and evaluation process that provides them security foresight before it is too late. A Post Breach Mindset is a lot like paying insurance. No one likes to pay until something disastrous happens.
What’s the Answer?
Once attackers have your data, they not only can demand a ransom but sell the data to your competitors. In 2019, the FBI found the average ransom payout was over $80,000 per attack.
Attackers have malware that dwells on a network for extended periods, infiltrating data they see as valuable and then deploying the ransomware with the aid of a control center. Attackers have learned to obfuscate their behaviors so thoroughly that any business can be ambushed at any time, without warning.
In the past, ransomware was all about a big splash, creating havoc, and demanding money. The sooner malware could encrypt and steal files, the better for the attackers. Ransomware has evolved into a sophisticated multifactor approach.
For Answers Contact Li Tech Solutions (516) 210-6400

Protect Your Company From Ransomware
Talk with any cyber-security expert and the prevailing method to circumvent a ransomware attack, backup, and encrypt your data on a schedule. Keeping your data safe and up to date is excellent advice but should be part of an overall layered strategy, not the only line of defense.
- Ryuk Ransomware is a multi-stage attack platform that uses a TrickBot trojan with its information stealing capabilities and lateral movement across the network. With Ryuk, an attacker could encrypt the entire machine and ransom data back to the victim.
- GandCrab, out of Japan now retired, controlled nearly 40% of all ransomware infections. Attackers could use stealth to update the code with new delivery mechanisms. GandCrab has now turned itself into a ransomware-as-a-service platform. Cyber-criminals log in and pay a fee to get the ransomware code.
- Sodinokibi exploits the vulnerabilities in servers and other digital assets. This ransomware is considered some of the most deadly code on record.
Recommendations
Use the 3-2-1 Rule with all data backups. Keep 3 complete copies of all company data, store 2 copies on different media. Keep 1 copy off-site in a location known only to upper management.
Train your organization to recognize the methods practiced by attackers. Make certain each employee can identify and knows how to remove phishing emails. Set up a chain of responsibility, so employees know who to turn to for guidance.
Implement endpoint security protocol protection for your network. The endpoint security space has matured from a simple antivirus program into a comprehensive defense strategy. Endpoint security identifies and manages data access over corporate networks.
Endpoint security platforms protect against fileless, file-based, and alternative types of malware.
Endpoints on the network such as laptops, mobile phones, and internet of things devices are encrypted against data leaks. A device that is not compliant with overall network protocols is provisioned with restricted access.
Li Tech Solutions is a premier solution provider against ransomware and other vicious malware code. Call immediately to speak with a skilled security professional (516) 210-6400

