Cybersecurity Solutions for Long Island Businesses: Managing Compliance and Mitigating Risks
Cybersecurity solutions are more critical than ever for Long Island businesses, with cyberattacks escalating to 480,000 incidents in 2022 alone. Compliance management within cybersecurity offers a structured approach to safeguarding your digital assets and maintaining operational integrity. This article outlines effective strategies to enhance your cybersecurity framework and ensure compliance.
Understanding Cyber Risk and Compliance on Long Island
As a business owner on Long Island, you’re well aware that cyber risks are not just theoretical threats—they are immediate challenges that can impact your operations, finances, and reputation. But what exactly constitutes a cyber risk? Any potential threat could lead to financial loss, disruption of your operations, or damage to your company’s reputation. This is due to failures or breaches within your information technology systems.
Long Island is dynamic, with businesses ranging from small local boutiques to sprawling tech firms. Each stores sensitive data that could be vulnerable to cyber-attacks. The need for a comprehensive cyber risk management strategy from a cybersecurity company like LI Tech has never been more critical. This strategy ensures your business operations comply with all the regulatory standards governing cybersecurity solutions.
Key Regulations Affecting Cybersecurity:
- Health Insurance Portability and Accountability Act (HIPAA): Ensures the protection of sensitive patient data for healthcare industries.
- Payment Card Industry Data Security Standard (PCI DSS): Mandatory security measures for entities that handle credit card information to reduce credit fraud.
- Federal Information Security Management Act (FISMA): Governs the protection of data and assets within federal government agencies.
- New York’s SHIELD Act: Requires businesses to implement specific security measures to protect the private information of New York residents.
When you understand all the regulations, you can implement the right cybersecurity solutions to better protect your company’s interests and keep your customers’ information safe.
Business IT Support on Long Island, NY

Key Cybersecurity Risks for Businesses on Long Island
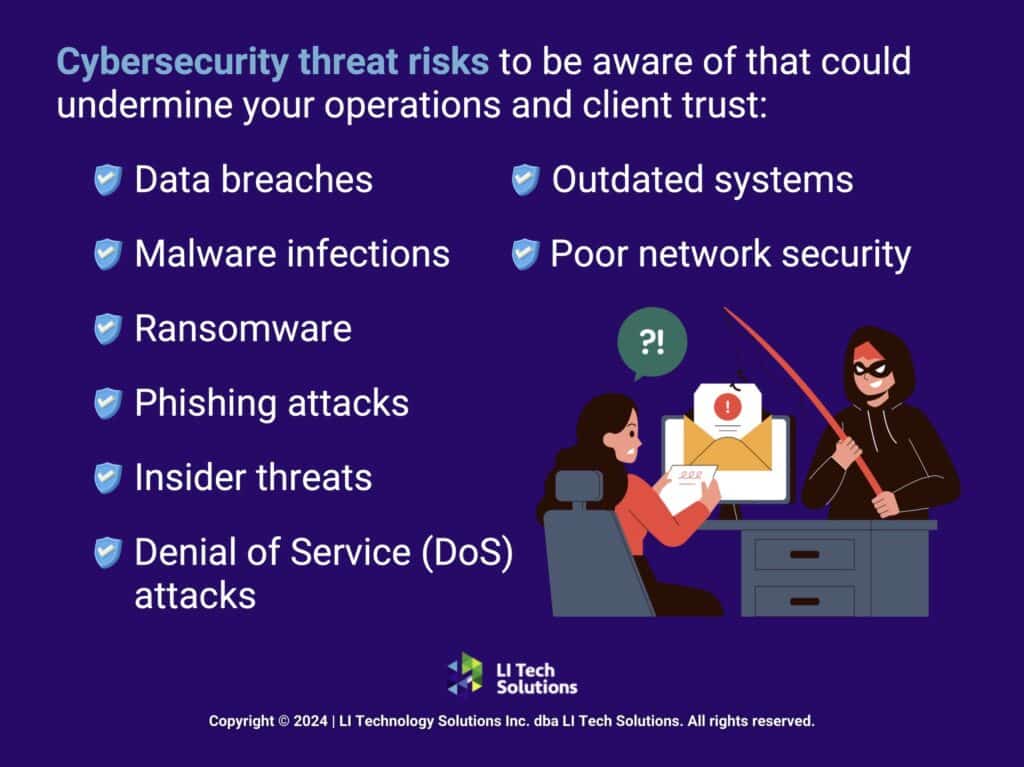
Just understanding the rules you need to follow isn’t enough. You also need to recognize the cybersecurity threats that could undermine your operations and client trust. Recognizing and understanding these risks is your first line of defense when it comes to cybersecurity solutions. Here are some specific cybersecurity risks that you should be aware of:
- Data Breaches: Any unauthorized access to your business data leads to the exposure of your customers’ sensitive information, trade secrets, or internal communication.
- Malware Infections: Malicious software can easily infect your system. If that happens, it leads to data theft, data integrity loss, and disruption of your operational abilities.
- Phishing Attacks: One of the most frequent ways cybercriminals get into your system is through fraudulent communications, often disguised as legitimate emails. Employees might not understand that they are really opening the door for outsiders to steal sensitive data such as login credentials and credit card numbers.
- Ransomware: A type of malware that locks you out of your systems, demanding a ransom to restore access, potentially crippling your business operations.
- Denial of Service (DoS) Attacks: These attacks work by flooding your systems with excessive traffic that overwhelms your resources and disrupts service. The result is a significant impact on your business availability.
- Insider Threats: Employees or contractors with access to corporate networks and data can become a threat if they maliciously or unintentionally breach security protocols.
- Poor Network Security: Weak security measures leave your network vulnerable to intrusions. It makes it easier for attackers to gain unauthorized access.
- Outdated Systems: When you put off updating your software and hardware, you are creating opportunities for vulnerabilities to remain in your system that cybercriminals can exploit.
At LI Tech, we offer Long Island managed IT services that focus on robust cybersecurity solutions designed to protect your business from these risks. When you partner with us for compliance as a service, you strengthen your defense mechanisms.
Top Cybersecurity Concerns for Long Island Businesses in 2025
The Role of Compliance Management in Cybersecurity Solutions
Compliance management is the structured process businesses follow to ensure they meet all the legal, regulatory, and technical standards related to cybersecurity. For companies on Long Island, staying compliant is not just about avoiding fines. You need to build a framework that enhances the security and integrity of your IT systems.
Here are a few key components of effective compliance management:
Regular Risk Assessments
Your business stays ahead of potential vulnerabilities by regularly conducting and updating risk assessments, with the help of LI Tech Solutions. This proactive approach means you’re always prepared for emerging threats. It also helps align your cybersecurity solutions with the latest industry standards. As threats evolve, your defenses need to as well.
Adherence to Standards
Compliance with established cybersecurity standards, like ISO 27001, NIST, and PCI DSS, is crucial for maintaining strong defenses against cyber threats. These standards provide a framework for managing the security of information assets, such as financial information, intellectual property, employee details, and information entrusted to you by third parties. Following these guidelines helps minimize risks and enhances your business’s credibility and trustworthiness in the eyes of customers and partners.
Employee Training
Human error remains one of the largest security vulnerabilities to any organization. Your company is not immune to this issue. By implementing regular training sessions, you give your employees the knowledge and skills they need to avoid these threats, including phishing attacks, password breaches, and other common cyber threats. Effective training reduces the likelihood of breaches and fosters a culture of security awareness throughout the organization.
These components form the backbone of a comprehensive compliance management system. And that system protects against the financial ramifications of non-compliance and strengthens your overall cybersecurity posture.

How Long Island Businesses Implement Proactive Cybersecurity Compliance
Training and internal compliance regulation alone aren’t enough to protect your systems. Achieving and maintaining compliance requires a proactive approach to cybersecurity solutions. This includes the integration of compliance tasks into daily workflows. Here’s how you can enhance your cybersecurity compliance from inside your IT system:
Implement Security Measures
Tailor your cybersecurity infrastructure to the unique needs of your business. Implement firewalls, advanced encryption, and state-of-the-art intrusion detection systems. These technologies serve as the first line of defense against cyber threats, safeguarding your critical data from unauthorized access and potential breaches. Regular updates and configuration adjustments are vital to adapt to the evolving cyber threat landscape, ensuring your defenses remain robust.
Regular Compliance Audits
Conduct scheduled compliance audits to uncover potential vulnerabilities and ensure continuous compliance with regulatory requirements. These audits provide a systematic review of your cybersecurity practices and policies, helping identify areas for improvement. Staying ahead of compliance through these audits protects you from penalties and reinforces your commitment to security for your clients and partners.
Engage With Managed IT Services
Partner with a Long Island managed service provider to leverage their expertise in maintaining compliance and managing complex IT environments. At LI Tech Solutions, we offer tailored IT consulting on Long Island and can handle the heavy lifting of compliance management, from routine monitoring to specific compliance-related tasks. This support is especially beneficial for businesses that may not have the resources to maintain a full-scale, in-house Long Island IT services department.

By following these steps, your business can establish a strong foundation for cybersecurity compliance, turning complex regulatory challenges into manageable tasks. Whether you’re enhancing current measures or building a new compliance strategy, remember that effective compliance is a continuous process that not only protects but also adds value to your business.
Secure Your Business’s Future: Take Action on Cybersecurity Compliance Today
If you’re running a business on Long Island, you know just how important it is to integrate robust cybersecurity solutions and compliance management into your operations. Not sure where to start? Contact LI Tech Solutions, one of the best cybersecurity companies on Long Island, NY. We ensure that your business is protected against today’s threats and prepared for tomorrow’s challenges. Secure your peace of mind by taking proactive steps toward effective cybersecurity compliance now.

