Ramping Up the Fight Against Ransomware
If you own a small or medium-sized business in Long Island, NYC, you may already know that ransomware could present a significant threat to your business. What is ransomware, exactly? Ransomware is software designed to render your files impossible to use. If you’re infected by ransomware, you won’t be able to use the information on your device or network until you pay what the attackers demand. This article details actions to help your business stay protected from ransomware.
Ransomware is constantly on the rise. It affects large corporations as well as smaller businesses in the Long Island, NYC area and across the globe. Ransoms are getting higher, too–the average payment rose 82% in 2021 from the previous year.
Working with an experienced IT team like LI Tech Solutions can help you protect your assets from ransomware attacks. However, there’s also a lot you can do to minimize risks. Let’s take a look at how you can effectively partner with your IT team and keep your business safe.
How can I prevent ransomware attacks? LI Tech Explains the basics
You can do a lot to keep ransomware attackers from impacting your business in the first place. Here are a few common-sense precautions you should never overlook in the fight to keep your business protected from ransomware.
Keep your software updated
Don’t ignore that software update prompt! Patches and updates can be annoying, but they are necessary to protect your devices and networks. It’s much harder for attackers to target a device that’s up to date. Automated patch management can make this much easier since you won’t have to remember to check for updates.
Keep your data in a secure location
Storing important data on just one device is asking for trouble. You should keep information on a separate device as a back-up. If ransomware attackers successfully target your primary data source, your information won’t be lost forever–and you won’t be stuck playing their games.
Educate everyone in your organization about social engineering strategies
What is social engineering? Simply put, it refers to techniques that trick users into giving attackers access to your information or systems. Social engineering can take many different forms. Here are a few of the most common.
- Phishing is a deceptive message, such as an email, that tricks users into clicking on a malicious link
- Baiting is any technique designed to use curiosity or greed to get users to grant restricted access to systems or information
- Pretexting occurs when a person with malicious intent pretends to be someone else, like an IT professional or auditor
Remember to avoid opening messages or clicking on links that seem suspicious. Frequent training will help everyone on your team know how to watch out for new strategies. Also, be sure to require proper email inbox filters to keep emails from attackers at bay.
Be proactive about following password guidelines
Using the same password everywhere you go is a good way to fall prey to ransomware attacks. Everyone in your organization should change their password frequently and follow proper complexity guidelines.

Where can I learn more about taking basic precautions?
The Cybersecurity and Infrastructure Security Agency is an American government agency devoted to cyber defense. Their website offers guidelines, resources and tools to help you stay protected.
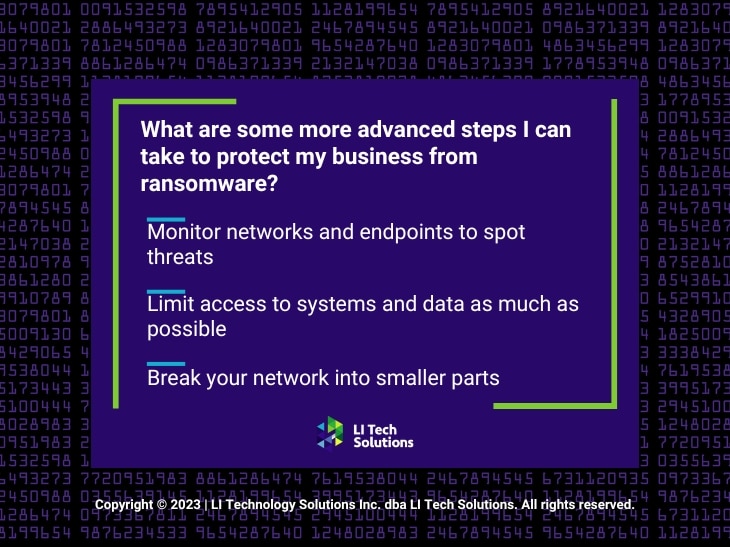
What are some more advanced steps I can take to protect my business from ransomware?
You know how to spot scam emails a mile away, and you’re aware that “12345” is not an acceptable password. However, there are also some less familiar steps that you should strongly consider to protect yourself from ransomware.
Monitor networks and endpoints to spot threats
What is an “endpoint”? In this context, it’s a device like a laptop or phone that might fall prey to attackers. Endpoint detection and response (EDR) is a process that can help you spot attacks on these devices quickly. You should also monitor your network routinely to avoid any blind spots. It’s important to perform routine scans to check for vulnerabilities in your systems that you may have overlooked.
Limit access to systems and data as much as possible
If everyone in your organization can access all of your information, you may need to improve your identity and access management techniques. Making sure your users have only the access they truly need is a great way to minimize threats.
Break your network into smaller parts
The more spread out your network is, the harder it is for attackers to deal a crushing blow. Segment your network into small pieces so that malicious attacks can only do so much damage.
4 Dangerous Ransomware Myths Proven False
How can my organization stay protected from ransomware while using devices that connect to the internet?
Everyone knows that the internet can be a dangerous place. When someone from your organization connects to the internet, they should take several precautions to prevent attacks.
- Install antivirus software and update it as needed
- Only use secure browsers to access the internet
- Always browse the internet with a firewall enabled
- Never use a public network to connect to the internet
- Never download a file if you can’t verify the source’s credibility
LI Tech Solutions: The Best NY MSP Partner Keeps You Protected From Ransomware
When you partner with LI Tech Solutions as your managed service provider, you’re working with industry leaders in data protection. We can help you effectively respond to attacks, but we can also ensure you take the proper protective measures to avoid ransomware attacks in the first place. Call us at 516.210.6400 today, and start working with the top IT service providers in Long Island, NYC.

